- Google Cloud
- Cloud Forums
- Apigee
- Re: Error getting oauth bearer token from service ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @dchiesa1 I am testing out the samples for cloud logging from my Apigee X Proxy. (I do have the other method working where we don't need to go the JWT route - but i still think this is valuable to get it up and running )I am having two issues.
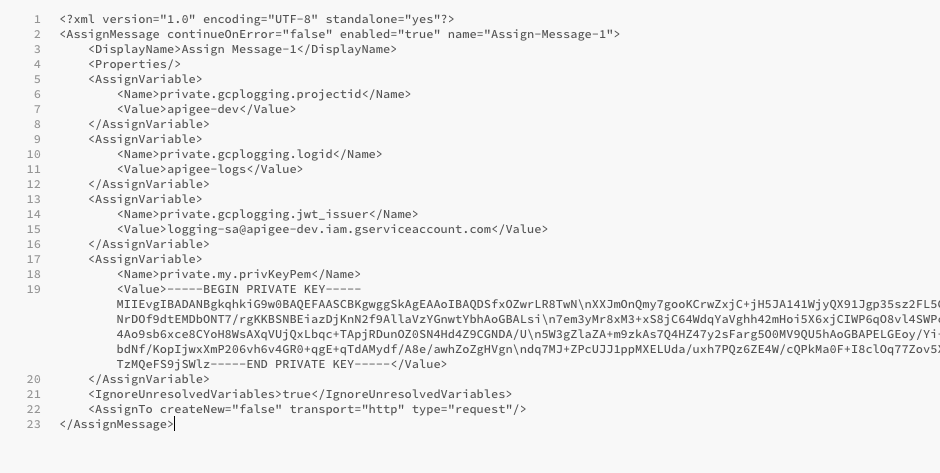
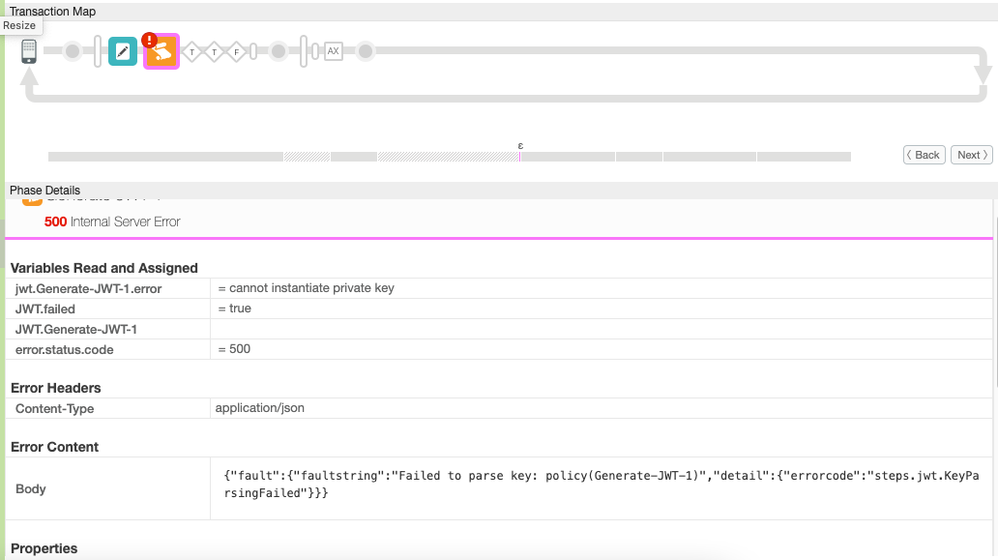
I have downloaded a service account key JSON key with the correct logging permissions. From there, i have - for simplicity - just hard coded it into the AssignMessage Policy. I have tried all the suggestions, from copying the private key into a private variable in the AssignMessage Policy with the "\n" removed ,replaced with backslashes and just creating everything as one line. However, all of them fail with the
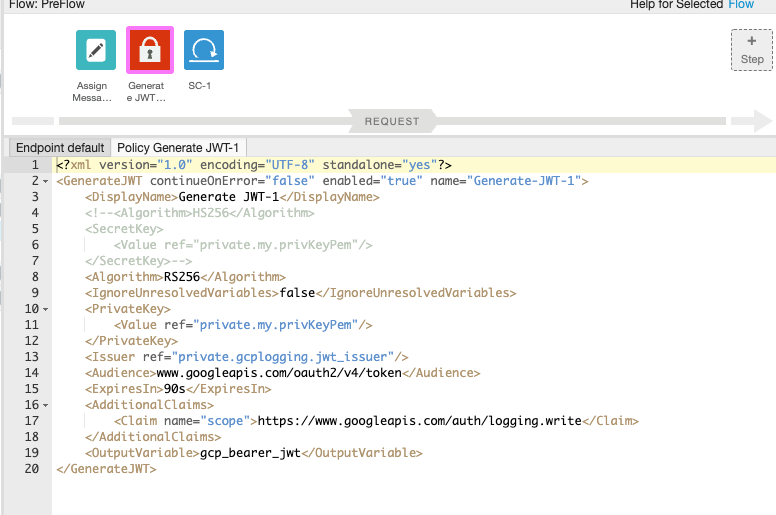
The funny thing is this step passes if I use the HS256 Algorithm, but thens the oauth token callout fails with a 400 error. I read somewhere that it only works if you use RS256 - hence I am stuck. If anyone has suggestions, I am open.
Thanks
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @dchiesa1 , sorry for the late response. First off, really want to take the time to thanks you for helping all of us out - really appreciate it. Secondly, this soln works great!! This fixed the problem of the formatting. I am now able to invoke the cloud logging API.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the screenshots, super helpful .
I have downloaded a service account key JSON key with the correct logging permissions. From there, i have - for simplicity - just hard coded it into the AssignMessage Policy. I have tried all the suggestions, from copying the private key into a private variable in the AssignMessage Policy with the "\n" removed ,replaced with backslashes and just creating everything as one line. However, all of them fail with the "Failed to parse key: policy(Generate-JWT-1)" error message. I am attaching some screen shots below
Yes, I think what you want is to replace the "\n" with newlines.
Let's suppose this is your .json file:
{
"type": "service_account",
"project_id": "gcp-project-001",
"private_key_id": "459f00670e8cc6598b06cf37",
"private_key": "-----BEGIN PRIVATE KEY-----\nMIIEvAIBADANBgkqhkiG9w0BAQEFAASCBKYwggSiAgEAAoIBAQCW6FM65yPCtn1A\n1663JqRIjOh+RudLT2HIM1yBEqQvWkwp0Lu/iq4PRm9DfYpIu0ugZkLnujMuFdRI\nkp7APWEuV7/IqQ6JbuW/6hZSV/l6csWhUXaC+Uk+rj/PFFMUlPRULvB2s2DdkSh9\nHAQI5tIOu3T86OxhjYW49KZ3ipLDxcDQzhINu9UCgYAslidKbtHEZci9WxXszboB\n+5OyuD1hY5rh9IUY0Fck/rNn7Me1HxNdsrx0+WNoiTw726diBEXdq7y1LqdG30xQ\nQ9F+lnd2b0xgzRtZuCqdpLYAGvFcpAat+lCLUwBYBbzJeBJl2I7YwQBJBGuWuXCX\nkmPObZQEAkB6GYIfO2fP0Q==\n-----END PRIVATE KEY-----\n",
"client_email": "account-name@gcp-project-001.iam.gserviceaccount.com",
"client_id": "11270269628840931",
"auth_uri": "https://accounts.google.com/o/oauth2/auth",
"token_uri": "https://oauth2.googleapis.com/token",
"auth_provider_x509_cert_url": "https://www.googleapis.com/oauth2/v1/certs",
"client_x509_cert_url": "https://www.googleapis.com/robot/v1/metadata/x509/account-name%40gcp-project-001.iam.gserviceaccount.com"
}
In the AssignMessage, you want something like this:
<AssignVariable>
<Name>private.my-private-key</Name>
<Value>
-----BEGIN PRIVATE KEY-----
MIIEvAIBADANBgkqhkiG9w0BAQEFAASCBKYwggSiAgEAAoIBAQCW6FM65yPCtn1A
1663JqRIjOh+RudLT2HIM1yBEqQvWkwp0Lu/iq4PRm9DfYpIu0ugZkLnujMuFdRI
kp7APWEuV7/IqQ6JbuW/6hZSV/l6csWhUXaC+Uk+rj/PFFMUlPRULvB2s2DdkSh9
HAQI5tIOu3T86OxhjYW49KZ3ipLDxcDQzhINu9UCgYAslidKbtHEZci9WxXszboB
+5OyuD1hY5rh9IUY0Fck/rNn7Me1HxNdsrx0+WNoiTw726diBEXdq7y1LqdG30xQ
Q9F+lnd2b0xgzRtZuCqdpLYAGvFcpAat+lCLUwBYBbzJeBJl2I7YwQBJBGuWuXCX
kmPObZQEAkB6GYIfO2fP0Q==
-----END PRIVATE KEY-----
</Value>
</AssignVariable>
I produce this with my text editor, just doing a find/replace on "\n" and replacing each one with a newline.
BUT
I have found an easier way to do things is just embed the entire .json file into a variable. Like this:
<AssignVariable>
<Name>private.service-account-json</Name>
<Value>
{
"type": "service_account",
"project_id": "gcp-project-001",
"private_key_id": "459f00670e8cc6598b06cf37",
"private_key": "-----BEGIN PRIVATE KEY-----\nMIIEvAIBADANBgkqhkiG9w0BAQEFAASCBKYwggSiAgEAAoIBAQCW6FM65yPCtn1A\n1663JqRIjOh+RudLT2HIM1yBEqQvWkwp0Lu/iq4PRm9DfYpIu0ugZkLnujMuFdRI\nkp7APWEuV7/IqQ6JbuW/6hZSV/l6csWhUXaC+Uk+rj/PFFMUlPRULvB2s2DdkSh9\nHAQI5tIOu3T86OxhjYW49KZ3ipLDxcDQzhINu9UCgYAslidKbtHEZci9WxXszboB\n+5OyuD1hY5rh9IUY0Fck/rNn7Me1HxNdsrx0+WNoiTw726diBEXdq7y1LqdG30xQ\nQ9F+lnd2b0xgzRtZuCqdpLYAGvFcpAat+lCLUwBYBbzJeBJl2I7YwQBJBGuWuXCX\nkmPObZQEAkB6GYIfO2fP0Q==\n-----END PRIVATE KEY-----\n",
"client_email": "account-name@gcp-project-001.iam.gserviceaccount.com",
"client_id": "11270269628840931",
"auth_uri": "https://accounts.google.com/o/oauth2/auth",
"token_uri": "https://oauth2.googleapis.com/token",
"auth_provider_x509_cert_url": "https://www.googleapis.com/oauth2/v1/certs",
"client_x509_cert_url": "https://www.googleapis.com/robot/v1/metadata/x509/account-name%40gcp-project-001.iam.gserviceaccount.com"
}
</Value>
</AssignVariable>And then access those constituent parts via a subsequent JS callout, like this:
<Javascript name='JS-Shred-Credentials'>
<Source>
var c = JSON.parse(context.getVariable('private.service-account-json'));
for (var prop in c) {
context.setVariable('private.' + prop, c[prop]);
}
</Source>
</Javascript>And then after running the AssignMessage policy and the subsequent Javascript policy, the variable private.private_key will contain something that can be parsed by the GenerateJWT policy.
ps: It definitely requires RS256 !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @dchiesa1 , sorry for the late response. First off, really want to take the time to thanks you for helping all of us out - really appreciate it. Secondly, this soln works great!! This fixed the problem of the formatting. I am now able to invoke the cloud logging API.
Thanks
-
Analytics
497 -
API Hub
75 -
API Runtime
11,665 -
API Security
178 -
Apigee General
3,041 -
Apigee X
1,288 -
Developer Portal
1,910 -
Drupal Portal
43 -
Hybrid
463 -
Integrated Developer Portal
89 -
Integration
310 -
PAYG
13 -
Private Cloud Deployment
1,069 -
User Interface
77

 Twitter
Twitter