- Google Cloud
- Cloud Forums
- Apigee
- Re: Apigee hide resources using IAM Condition Poli...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've created a custom Role for a group with this privileges:
apigee.deployments.get apigee.deployments.list apigee.entitlements.get apigee.envgroupattachments.get apigee.envgroupattachments.list apigee.envgroups.get apigee.envgroups.list apigee.environments.get apigee.environments.getStats apigee.environments.list apigee.operations.get apigee.operations.list apigee.projectorganizations.get
So I need users who belong to this group to ONLY see (and work with) some ENVIRONMENTS in the Apigee UI (and obviously only privileges in those environments).
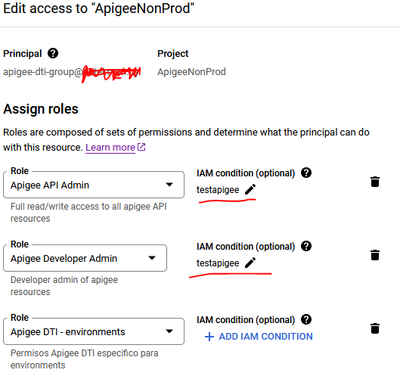
I made this IAM conditions policies:
resource.name.startsWith("organizations/{org}/apis/dti-") ||
resource.name.startsWith("organizations/{org}/sharedflows/dti-") ||
resource.name.startsWith("organizations/{org}/environments/dti-") ||
(
resource.name.startsWith("organizations/{org}/apis/dti-test/keyvaluemaps") &&
resource.type == "apigee.googleapis.com/KeyValueMap"
) ||
(
resource.name.startsWith("organizations/{org}/apiproducts/dti-") &&
resource.type == "apigee.googleapis.com/ApiProduct"
) ||
resource.type == "cloudresourcemanager.googleapis.com/Project"
This works for API proxies and shared flows, but I can't reproduce this same solution for environments.
Is there documentation for this specific area or maybe some examples to try?
Thanks.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Acesss to environment level resources is actually not controlled by IAM conditions. Rather it is controlled by access granted to each individual environment through the Apigee UI or API. You can learn more in this excellent article from my colleague @kurtkanaskie. Below is the relevant excerpt.
Environments do not support conditional role assignment directly. Rather, access to an environment and its resources is granted via “Access” in the UI or via the Apigee API Environments Set IAM Policy API. Assigning a user as an “Apigee Environment Admin” to an environment (e.g. bu1-test) controls access to environment specific resources such as KVMs, Resource files, TargetServers, References, and KeyStores. It also controls access to deployments and debug sessions for the environment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Acesss to environment level resources is actually not controlled by IAM conditions. Rather it is controlled by access granted to each individual environment through the Apigee UI or API. You can learn more in this excellent article from my colleague @kurtkanaskie. Below is the relevant excerpt.
Environments do not support conditional role assignment directly. Rather, access to an environment and its resources is granted via “Access” in the UI or via the Apigee API Environments Set IAM Policy API. Assigning a user as an “Apigee Environment Admin” to an environment (e.g. bu1-test) controls access to environment specific resources such as KVMs, Resource files, TargetServers, References, and KeyStores. It also controls access to deployments and debug sessions for the environment.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,664 -
API Security
177 -
Apigee General
3,037 -
Apigee X
1,283 -
Developer Portal
1,909 -
Drupal Portal
43 -
Hybrid
463 -
Integrated Developer Portal
89 -
Integration
309 -
PAYG
13 -
Private Cloud Deployment
1,068 -
User Interface
76
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter