- Google Cloud Security
- Google Security Operations
- Google Security Operations Forums
- SIEM Forum
- Re: YARA-L, Rule Schreiben
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
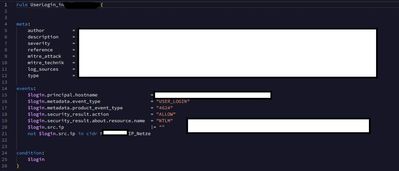
Hi,
i have wrotten a new Rule, but it shows always 2 or more Events/Alerts. I want to see only one Event at a succesfully Login. I have posted Screenhot. How can i configure it?
Best regards
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In the original email, you mention multiple events/alerts. As I read through this thread, as Dan points out, we can't solve multiple 4624 events from Microsoft being logged (at least not at the rule level), but we can roll those multiple events being generated into a single detection/alert using the match section in a rule.
By adding a placeholder variable(s) in the events section, like these for example
$login.target.user.userid = $userid
$login.principal.hostname = $hostname
We could then add a match section
match:
$hostname over 5m
match:
$userid over 5m
match:
$hostname, $userid over 5mAnd the result would be that all events that match the criteria in the event section are grouped by whatever value(s) are in the match section over the defined period of time.
Here is a quick video on aggregation that might be helpful: https://www.googlecloudcommunity.com/gc/Chronicle-Best-Practices/Getting-to-Know-Chronicle-SIEM-Aggr...
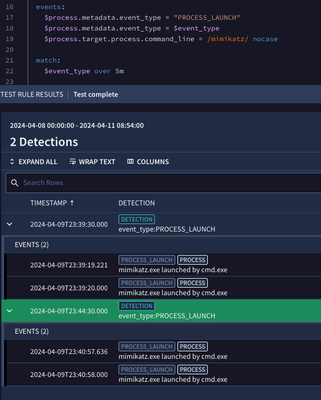
This isn't like for like, but an example on mimikatz and process launches that might help as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you getting two 4624 events?
I guess a better question is what are the events if you do a login and then a test run for that time period?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
when I login, there are four events in 5 seconds. My Question is: How can i write a rule, that is 1 Login = 1 Detection
Must i use "over"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don’t believe this a rule problem - it’s a Microsoft problem.
Quick google search shows multiple people with similar experiences.
https://www.nextofwindows.com/several-log-entries-of-event-4624
Also, when you look in the windows logging console are the events your username or system? If they are both, you can filter out the system account with a NOT statement in your rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Event ID's.
Several of them are related to user - SYSTEM. You may want to filter that
out and use domain/regex or something for username.
--
Thank you,
DN - dnehoda@google.com
440.787.1307
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In the original email, you mention multiple events/alerts. As I read through this thread, as Dan points out, we can't solve multiple 4624 events from Microsoft being logged (at least not at the rule level), but we can roll those multiple events being generated into a single detection/alert using the match section in a rule.
By adding a placeholder variable(s) in the events section, like these for example
$login.target.user.userid = $userid
$login.principal.hostname = $hostname
We could then add a match section
match:
$hostname over 5m
match:
$userid over 5m
match:
$hostname, $userid over 5mAnd the result would be that all events that match the criteria in the event section are grouped by whatever value(s) are in the match section over the defined period of time.
Here is a quick video on aggregation that might be helpful: https://www.googlecloudcommunity.com/gc/Chronicle-Best-Practices/Getting-to-Know-Chronicle-SIEM-Aggr...
This isn't like for like, but an example on mimikatz and process launches that might help as well.
-
Admin
24 -
AI
1 -
API
16 -
Applied Analytics
2 -
BigQuery
3 -
Browser Management
2 -
Chrome Enterprise
2 -
Chronicle
10 -
Compliance
5 -
Curated Detections
9 -
Custom List
1 -
Dashboard
9 -
Data Management
32 -
Ingestion
46 -
Investigation
24 -
Logs
2 -
Parsers
52 -
Rules Engine
65 -
Search
30 -
SecOps
2 -
Security Command Center
1 -
SIEM
20 -
Siemplify
1 -
Slack
1 -
Threat Intelligence
18
- « Previous
- Next »

 Twitter
Twitter