- Google Cloud
- Cloud Forums
- Apigee
- Secure communication channel between Apigee and GK...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi everyone,
I try to include Apidge EDGE into my company API request processing chain.
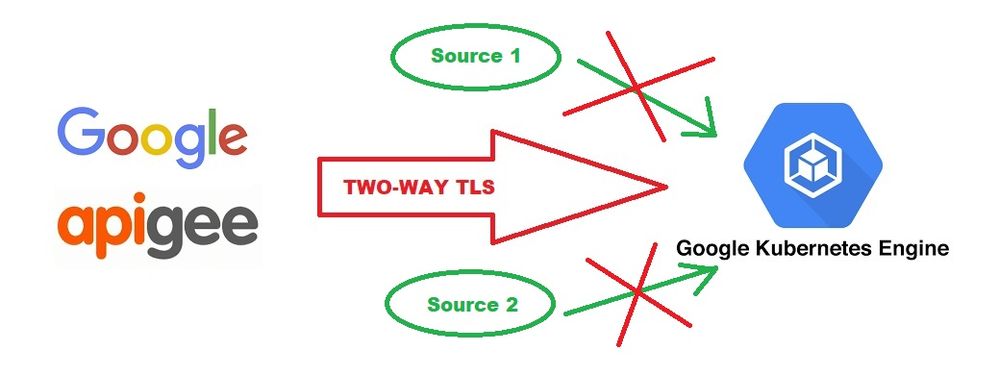
But, the main questions: how to establish communication between Apigee EDGE and Google Kubernetes Engine Ingress as it shown on the attached picture?
It means,
1. It is necessary to organize certificate authentication on back-end side.
2. Usage of client certificates on front end side.
3. Prevent ability of non-Apigee apps to get success responses with required data from back-end server through ingress.
First of all, it is necessary to note:
1. Server and client certificates will be generated as it is described there: https://kubernetes.github.io/ingress-nginx/examples/PREREQUISITES/#client-certificate-authentication
2. Ingess and secret will be created as it is described there:
https://kubernetes.github.io/ingress-nginx/examples/auth/client-certs/
3. I will use payed account, therefore, I can create virtual hosts.
Problems,
1. GKE Ingress does not return ERROR 400 if I sent wrong certs, as It does Nginx on ssl_verify_client on set. It returns requested data.
2. I cannot create virtual host with certs generated using provided above way.
Questions:
1. How to correctly configure GKE ingress to prevent side servers requests?
2. How to create virtual host with client serts generated using provided above way?
This questions are crucial for Apigee application in bussiness, and, may be they are for Apigee team members. I need to have safe channel only between Apigee and GKE Ingress.
I read answers on questions, like:
https://community.apigee.com/questions/40286/what-is-the-best-practice-for-securing-communicati.html
but they are very general.
Guys, how to apply payed Apigee? I cannot see a way.
Thank you in advance!
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On the Apigee side of things you've mentioned virtual hosts a few times, but that isn't consistent with the description of what you're trying to achieve.
Your request flow is described like this:
Client -> Apigee -> GKE
but Virtual Hosts are on the side of Apigee closest to the client ("northbound"). To configure the Apigee side of the connection to GKE ("southbound") you need to configure your target endpoint (see https://docs.apigee.com/api-platform/reference/api-proxy-configuration-reference#tlsssltargetendpoin... ) to use the correct client key & certificate to talk to GKE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On the Apigee side of things you've mentioned virtual hosts a few times, but that isn't consistent with the description of what you're trying to achieve.
Your request flow is described like this:
Client -> Apigee -> GKE
but Virtual Hosts are on the side of Apigee closest to the client ("northbound"). To configure the Apigee side of the connection to GKE ("southbound") you need to configure your target endpoint (see https://docs.apigee.com/api-platform/reference/api-proxy-configuration-reference#tlsssltargetendpoin... ) to use the correct client key & certificate to talk to GKE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, I haven't seen answer. And forgot to write solution there. Sorry guys.
Yes, I used this way and all works fine .
I used Nginx Ingress controller as it is described there https://kubernetes.github.io/ingress-nginx/examples/auth/client-certs/
used and <TargetEndpoint... <SSLInfo>... as it described in provided above link.
For certs generation use this link: https://kubernetes.github.io/ingress-nginx/examples/PREREQUISITES/#client-certificate-authentication
All is working.
No need in aditional virtual hosts.
Nevertheless I haven't seen it, thank you for answer. I think it will be useful for other people.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,660 -
API Security
174 -
Apigee General
3,020 -
Apigee X
1,263 -
Developer Portal
1,906 -
Drupal Portal
43 -
Hybrid
459 -
Integrated Developer Portal
87 -
Integration
308 -
PAYG
13 -
Private Cloud Deployment
1,067 -
User Interface
75
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter