- Google Cloud
- Cloud Forums
- Apigee
- Mutual TLS to backend server with Self-signed Cert
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I am currently testing Mutual TLS between Apigee Edge and a backend with a self signed certificate. The self-signed certificate is just for testing and and a signed cert will be used in Prod.
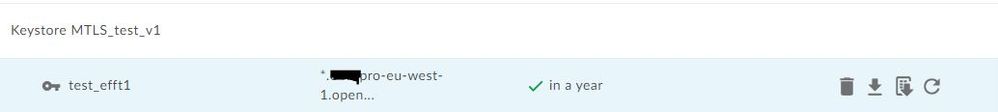
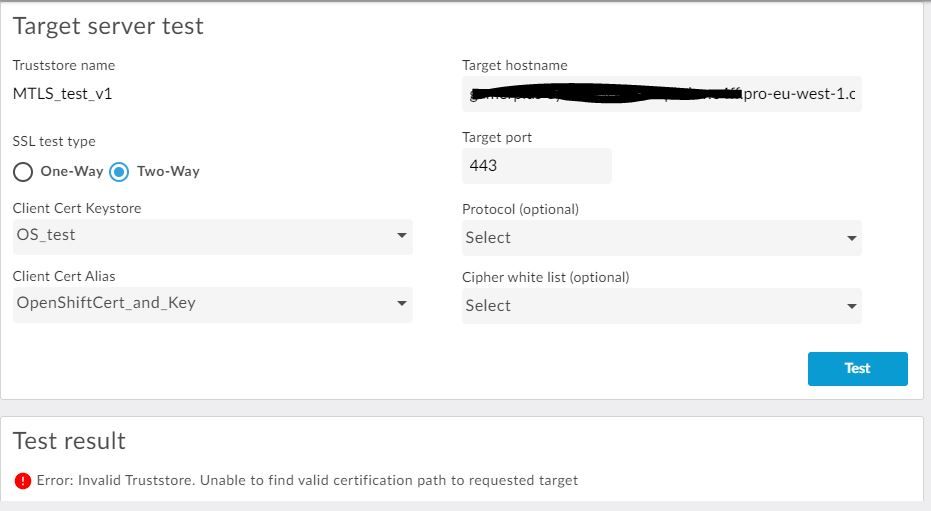
So I have configure the Keystore with the Server cert and key and also created a truststore with only the server cert. When testing the certs in the UI I keep on getting the following error: Error: Invalid Truststore. Unable to find valid certification path to requested target
I have done a couple of mutual TLS integrations to backend with CA signed Certs, but this is the first with a Self-signed cert.
How do you need to setup the Truststore for this to work? To generate the selfsigned cert i used the following command: openssl req -x509 -newkey rsa:4096 -nodes -out cert.pem -keyout key.pem -days 365
- Labels:
-
API Runtime
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am not specifically familiar with the particular error you're seeing: eg, "Invalid Truststore".
This message suggests that the truststore itself is not valid. What might cause this?
Maybe the cert you've loaded into the truststore is not a valid x509v3 cert? Maybe it's misformatted.
Can you verify for me how you loaded that cert.pem into the Truststore? Show me what you did?
And can you show me what the Admin UI shows you when you view that truststore?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dino,
When creating a Keystore, I used two methods.
Method1: Used the Self-signed dropdown item and left everything default with a CommonName of *.something.pro-eu-west-1.openshiftapps.com
When I run the test function on the UI I get the error mentioned
Method2: I selected certificate only and uploaded the server.crt that was generated from the following command: openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
When I do a openssl s_client -connect -showcerts <url:port> I have noticed the following:
---
Server certificate
subject=/CN=*.sometext.pro-eu-west-1.openshiftapps.com
issuer=/C=US/O=Let's Encrypt/CN=Let's Encrypt Authority X3
---
No client certificate CA names sent
Peer signing digest: SHA512
Server Temp Key: ECDH, P-256, 256 bits ---
SSL handshake has read 3249 bytes and written 302 bytes
Verification error: unable to get local issuer certificate
---
When I view from the UI
When I run a test on that Keystore, I get the following:
Just to verify, just to make sure I didn't make a rookie error, I have created a Keystore with the cert and key that is required for the Backend server, because it is a self-signed cert I had to create a Truststore and add the self-signed cert to it. I then tested the connection from the truststore.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,661 -
API Security
174 -
Apigee General
3,021 -
Apigee X
1,263 -
Developer Portal
1,906 -
Drupal Portal
43 -
Hybrid
459 -
Integrated Developer Portal
87 -
Integration
308 -
PAYG
13 -
Private Cloud Deployment
1,067 -
User Interface
75
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter