- Google Cloud
- Cloud Forums
- Apigee
- Secure Apigee Edge proxy with keycloak?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am using two-way TLS communication between Apigee Edge and Backend server (which is exposed using NginxIngress in Kubernetes). However, we want to integrate Apigee Edge with keycloak to secure the endpoint (e.g https://org-name-env.apigee.net/path).
We have users, roles, and realms created on Keycloak and all of the users are managed through that. Credentials and tokens are also provided using Keycloak to all the developers (or Users with different roles).
How can I ask Keycloak or Apigee to verify the JWT token sent by the client without any code changes in the backend?
We want to implement Bearer only authentication. Keycloak issues the token, and then the client includes that (bearer) token in the request that is sent to Apigee Edge. We want Apigee Edge to validate that token.
I am new to Apigee and Keycloack and after searching a lot, I am posting this question to get proper documentation on using Keycloak with Apigee Edge. Any article, community answers, documentation or POC will be helpful. Thanks.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Keycloak, I believe, can act as an OpenID Connect provider.
This means that
- Keycloak issues client credentials (client ID's and maybe secrets, or private keys)
- Keycloak can generate an ID Token (JWT) when a user signs in
Maybe you want Apigee Edge to validate the ID Token generated by KeyCloak. If so, then, in your Apigee Edge API Proxy,
- use the VerifyJWT policy, and specify the public key of Keycloak, or specify the JWKS that Keycloak exposes. This will verify that the token being sent in was generated by Keycloak.
- Once you have verified the JWT, you can examine and validate the claims. If you would like to validate the client id, you can do that. (But strictly speaking this is not necessary as Keycloak has issued the JWT., and the VerifyJWT has verified the signature. Therefore Apigee Edge can be assured that the client id is valid in the Keycloak system). You can also validate any of the other claims in the JWT - subject, audience, or whatever. All of this is up to you. Validation in this case might mean "checking the value against a range of valid values" or it could be "checking that the value exists" or .. something else. It's up to your application needs.
- If everything succeeds, you can proxy the call to a backend system.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Need more details. What are you trying to do with KeyCloak? What is the use case? Are you wanting to use it for oauth and OpenID connect? Social Login? or something else? You wrote "to secure the endpoint" but unfortunately that description doesn't help much. Apigee Edge can secure the endpoint for you by itself using oAuth. So not sure what you are asking. Again, just need more details on the use case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry for the ambiguity. Apigee Proxy Endpoint is pointing to a backend server which is REST API server, so by securing Proxy Endpoint with Keycloak, I mean to secure the REST API using KeyCloak which will be a token-based authentication ( or the best way to authenticate requests coming to the REST Endpoints). We want to do the authentication part before even the request reaches to the backend so that we can monitor the "number of failed attempts" (Number of requests with failed authentication. Is this possible to monitor using Apigee Edge?)
I understand that Apigee Edge is enough to authenticate the request on its own without using Keycloak, but we want to use Keycloak for this purpose.
Long story short: my question is "How to secure an Apigee Edge Proxy Endpoint (e.g https://org-name-env.apigee.net/path and this URL is pointing to a REST API) using Keycloak?".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Got it. Thank you for the clarification. To answer your follow up question, "Is this possible to monitor using Apigee Edge?"
Yes! It is possible. Edge has built in monitoring so you could set up Edge as an Authorization server and have it issue tokens. Then, for all requests to your proxies, you could set up monitoring for 401 and 403 status codes and send alerts to email, slack, pager duty, and webhook. Check the Apigee documentation here.
So, if monitoring for failed AuthZ and AuthN is all you need from KeyCloak, then perhaps KeyCloak isn't needed? Edge also has analytics so you can create a report to view how many of these events are happening hourly, daily, etc... and also break it out by client app.
Does this answer your question? If not, please feel free to add any additional details or questions. Otherwise, please click accept so the question will be closed as answered.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the answer to the follow-up question. However, we do want to use Keycloak for securing the Apigee Edge Endpoint (which is a proxy for a REST API server) and I am yet to find a well-written documentation/article/post on how to integrate Keycloak with Apigee Edge to secure Proxy Endpoint (Using token based authentication or any other best way of doing the same).
Please point me to a documentation or any thing which will make the setup easy for me. I don't have a direction right now on how to integrate Keycloak and Apigee Edge.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok. Is KeyCloak between client and Edge? Or is KeyCloak between Edge and target (backend server).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Keycloak is between Client and Edge. @Robert Johnson would you please point me to a direction on how to configure this setup.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Amit Yadav. Typically customers put a WAF in front of Edge so haven’t seen much about an Auth server in front of Edge.
It sounds like clients will be connecting to KeyCloak first and then KeyCloak will call to edge correct? Edge would then call to the backend API servers.
So what about client IDs and Secrets? Does KeyCloak have a developer portal for them to get their credentials? If so, it sounds like all you want is to secure from KeyCloak to edge. In that case you could use HMAC or Mutual TLS or JWT. Can KeyCloak support any of those options to its targets?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tagging @Dino-at-Google @Anil Sagar @ Google and @Siddharth Barahalikar for help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Amit Yadav, I did not work on Keycloak. I would give you a generic answer on how to use external tokens in Apigee.
Will the Client pass Keycloack Token in the request to Apigee?
If yes, then on Apigee use a Service Callout policy to call the Introspect API of Keycloak to get the incoming token verified.
If no, you need to create two flows one to generate the token by passing and calling the Authorization API in Keycloak and the other flow to verify(introspect) the token.
The drawback of using an external authorization system is that you'd lose out on developer- and app-specific metrics and targeted traffic control (like quota), monetization because Apigee needs to know about the developers and apps.
A workaround to the above drawback is to import externally generated access tokens, refresh tokens, or auth codes into the Edge token store. You can use this technique if you would like to configure Apigee Edge to validate tokens that are generated outside of Apigee Edge.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Amit Yadav, I agree to the suggestion given by @Siddharth Barahalikar, and would like to add that in service callout if you are doing proxy chaining, then you will get the missed features in the chained proxy for Keycloak.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Anil Sagar @ Google @Siddharth Barahalikar @Dino-at-Google @Robert Johnson @Priyadarshi Ajitav Jena all of the resources and links that I find regarding keycloak, I see code changes on the backend is involved to do Bearer only authentication using keycloak.
We have users, roles, and realms created on Keycloak and all of the users are managed through that. Credentials and tokens are also provided using Keycloak to all the developers (or Users with different roles).
How can I ask Keycloak or Apigee to verify the JWT token sent by the client without any code changes in the backend?
We want to implement Bearer only authentication in Keycloak and then the request reachs to Apigee. Any links to documentation or article will be helpful. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Keycloak, I believe, can act as an OpenID Connect provider.
This means that
- Keycloak issues client credentials (client ID's and maybe secrets, or private keys)
- Keycloak can generate an ID Token (JWT) when a user signs in
Maybe you want Apigee Edge to validate the ID Token generated by KeyCloak. If so, then, in your Apigee Edge API Proxy,
- use the VerifyJWT policy, and specify the public key of Keycloak, or specify the JWKS that Keycloak exposes. This will verify that the token being sent in was generated by Keycloak.
- Once you have verified the JWT, you can examine and validate the claims. If you would like to validate the client id, you can do that. (But strictly speaking this is not necessary as Keycloak has issued the JWT., and the VerifyJWT has verified the signature. Therefore Apigee Edge can be assured that the client id is valid in the Keycloak system). You can also validate any of the other claims in the JWT - subject, audience, or whatever. All of this is up to you. Validation in this case might mean "checking the value against a range of valid values" or it could be "checking that the value exists" or .. something else. It's up to your application needs.
- If everything succeeds, you can proxy the call to a backend system.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is by far the simplest and best answer. Solved my problem, I was able to integrate KeyCloak with Apigee using JWT Token. Thank you @Dino-at-Google
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm glad to help.
One additional wrinkle to keep in mind: You are using VerifyJWT, and because your proxy trusts KeyCloak (trusts its public key), your proxy can be assured that all the claims in the JWT are valid, that it is not expired, and so on. All of that is fine.
But, if you do not invoke the VerifyApiKey** policy in Apigee Edge, then you won't be able to see per-app and per-developer analytics in Apigee Edge. This may be something you care about, and maybe not.
(**or VerifyAccessToken, but this would apply only to tokens issued by Apigee Edge)
VerifyApiKey checks that a value is a valid api key in Apigee Edge. If it is, then all of the analytics data gets logged against that developer app, developer, product, and so on.
But we already said that KeyCloak is the thing that is issuing client credentials - client id (aka API Key) and secret. So ... how could you use Apigee Edge to validate a client id that is really known only by KeyCloak ?
To do that, you need to "import" the client id (API Key) into Apigee Edge. https://community.apigee.com/questions/54291/how-to-create-an-app-with-an-external-clientid-and.html
Then, alter your proxy so that immediately after the VerifyJWT, you use VerifyApiKey on the variable that holds the claim that stores the KeyCloak client id that has been imported into Apigee Edge. That would give you API analytics in Apigee Edge.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just tried your solution. So far so good.
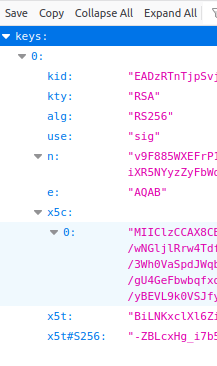
The documentation shows I should be able to use the JWKS uri like this:
<PublicKey> <JWKS uri="https://REDACTED/auth/realms/SUVI/protocol/openid-connect/certs"/> </PublicKey>
However this fails with the error message:
{"fault":{"faultstring":"Invalid Key configuration : policy(VerifyKeycloakJWT) element(PublicKey)","detail":{"errorcode":"steps.jwt.InvalidKeyConfiguration"}}}
The returns this:
What am I doing wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nevermind. I think I found my problem. I am using a self-signed certificate for the JWKS enpoint.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
GREAT, glad to hear it.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,662 -
API Security
175 -
Apigee General
3,027 -
Apigee X
1,270 -
Developer Portal
1,906 -
Drupal Portal
43 -
Hybrid
459 -
Integrated Developer Portal
87 -
Integration
308 -
PAYG
13 -
Private Cloud Deployment
1,067 -
User Interface
75
| User | Count |
|---|---|
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter