- Google Cloud
- Cloud Forums
- Apigee
- Dev portal invocation - External OAuth
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
I created a few proxies and exposed them on an Apigee evaluation account.
Those APIs needs OAuth2.0 security and client_credentials grant type, with an external OAuth server.
When I invoke those proxies it works (I use an Insomnia REST client). I configured the "Access Token URL" , "client_id" and "client_secret" in the security tab of the client and everything works fine.
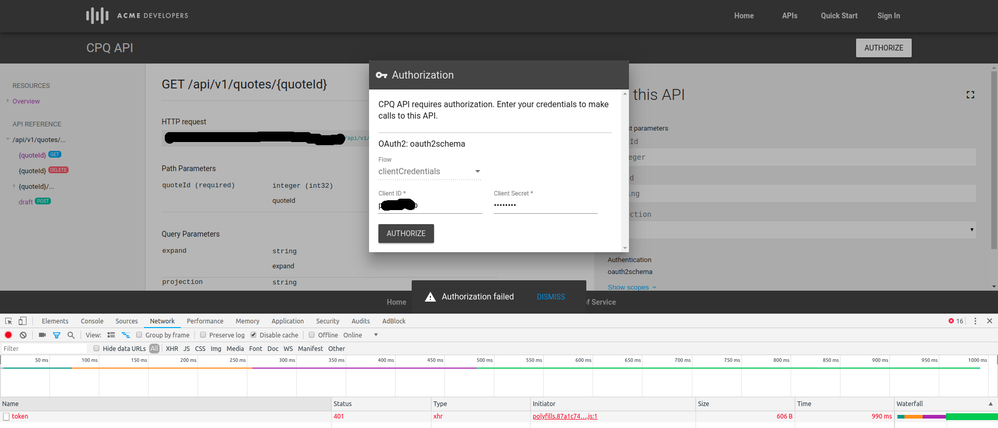
The problem arises when I want to make the call from the Developer Portal.
I configured the API Spec with proper values:
"securityDefinitions": {
"oauth2schema": {
"type": "oauth2",
"flow": "application",
"tokenUrl": "PROTOCOL_AND_HOST_OAUTH_SERVER/oauth/token",
"scopes": {
"test": "test"
}
}
}But when I try to authorize the request to the API from the portal, I get an error HTTP 401.
First weird thing I see, is that the portal is making an OPTIONS HTTP request to get the token, not a regular POST. And I believe that is not sending the credencials, but I'm not sure of that.
Is this feature working? What am I missing?
Thanks in advance!
Juan
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think maybe it is THE BROWSER that is making the OPTIONS request.
The OPTIONS Call is a CORS preflight request.
The browser sends this automatically, when it is necessary. For example when JavaScript code loaded by a web page in the browser attempts to POST to an origin (hostname) that is not the origin from which the page was served, the browser will automatically send out the CORS preflight request, prior to sending the POST. The browser will send the POST if and only if the response to the CORS preflight indicates that it is safe.
I think this is what is happening to you. The devportal page is loaded from your devportal URL. But the /token endpoint is a different URL. Therefore the browser concludes a CORS preflight is necessary. The /token endpoint is not handling the CORS preflight, and so the browser is short-circuiting the POST to the token endpoint. It is not making that POST. Result: you can't get a token.
There is no way for you to tell the browser "don't do that CORS preflight thing".
The only solution is to have your server , the thing listening at PROTOCOL_AND_HOST_OAUTH_SERVER , correctly handle and respond to the CORS preflight. If the oauth server is an Apigee Edge API Proxy, then you can look here for how to do it.
The reason your calls work from Insomnia is that Insomnia is not bound by the Cross-Origin Request Sharing (CORS) spec that is used by every bonafide web browser. Unlike Chrome, IE, Safari, Firefox, and so on, the Insomnia client doesn't load web pages. (I don't know Insomnia, I'm just guessing) Therefore Insomnia can call any endpoint it likes, and never needs to send a CORS preflight.
BTW, This CORS preflight stuff is not an Apigee Edge thing, this is not a behavior that is unique or particular to the Apigee Edge developer portal. This is just standard browser security.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think maybe it is THE BROWSER that is making the OPTIONS request.
The OPTIONS Call is a CORS preflight request.
The browser sends this automatically, when it is necessary. For example when JavaScript code loaded by a web page in the browser attempts to POST to an origin (hostname) that is not the origin from which the page was served, the browser will automatically send out the CORS preflight request, prior to sending the POST. The browser will send the POST if and only if the response to the CORS preflight indicates that it is safe.
I think this is what is happening to you. The devportal page is loaded from your devportal URL. But the /token endpoint is a different URL. Therefore the browser concludes a CORS preflight is necessary. The /token endpoint is not handling the CORS preflight, and so the browser is short-circuiting the POST to the token endpoint. It is not making that POST. Result: you can't get a token.
There is no way for you to tell the browser "don't do that CORS preflight thing".
The only solution is to have your server , the thing listening at PROTOCOL_AND_HOST_OAUTH_SERVER , correctly handle and respond to the CORS preflight. If the oauth server is an Apigee Edge API Proxy, then you can look here for how to do it.
The reason your calls work from Insomnia is that Insomnia is not bound by the Cross-Origin Request Sharing (CORS) spec that is used by every bonafide web browser. Unlike Chrome, IE, Safari, Firefox, and so on, the Insomnia client doesn't load web pages. (I don't know Insomnia, I'm just guessing) Therefore Insomnia can call any endpoint it likes, and never needs to send a CORS preflight.
BTW, This CORS preflight stuff is not an Apigee Edge thing, this is not a behavior that is unique or particular to the Apigee Edge developer portal. This is just standard browser security.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,660 -
API Security
174 -
Apigee General
3,020 -
Apigee X
1,263 -
Developer Portal
1,906 -
Drupal Portal
43 -
Hybrid
459 -
Integrated Developer Portal
87 -
Integration
308 -
PAYG
13 -
Private Cloud Deployment
1,067 -
User Interface
75
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter