- Google Cloud
- Cloud Forums
- Apigee
- Error while using Generate JWT policy in Apigee b...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello ,
I am trying to generate a JWT token using Apigee Generate JWT policy with RSA256 algorithm and getting the following error
| jwt.Generate-JWT-1.error | cannot instantiate private key |
|---|
I am able to generate and verify a JWT using HS256. I saw in the community that people faced the same issue and no one has generated a JWT with RS256. Is this issue solved or I am I missing something?
FYI we are on private cloud version 4.18.1, is the fix applied to this version?
Please let me know, if I am missing something.
Thanks in advance for your time.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Dino Sorry for late response, we found why it is failing.
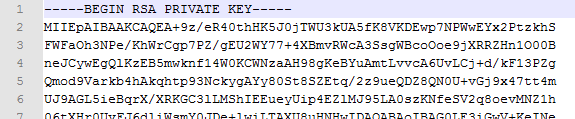
we were generating the private key using following command,
"openssl genrsa -out private-encrypted-rsa-des.pem 2048" -This doesn't show the algorithm in private key.
pic.1
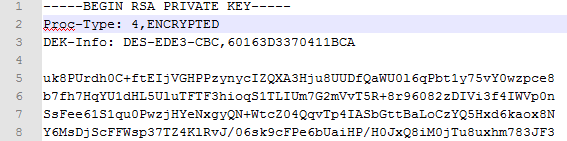
But when we use the following command,
"openssl genrsa -des3 -out private-encrypted-rsa-des3.pem 2048" -This show's the algorithm in private key.
pic.2
By using the private key(in pic.2) we were able to successfully generate & validate the JWT token.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, thanks for the reply. I'm glad it's working for you.
We're working on making this more tolerant of the various PEM formats. Improvements are coming so that you will be able to use the old RSA format, encrypted keys, unencrypted keys, and new formats for both. Much more flexible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi hemanth
I understand you're having trouble with the GenerateJWT policy. Sorry about that. The error message indicates that the policy cannot instantiate the private key.
I saw in the community that people faced the same issue and no one has generated a JWT with RS256.
I think this is not correct. It's not correct that "no one has generated a JWT with RS256". Plenty of people are doing that.
You didn't describe how the private key is formatted. There are multiple options, of course. It needs to be PEM-encoded, using either PKCS#1 or PKCS#8. There's a really good review of these options on stackoverflow.
One limitation with the original policy was in de-serializing encrypted private keys. The original policy was able to de-serialize encrypted private keys, if and only if DES3 encryption was used. In PKCS#1 format, an encrypted key that could be deserialized looked like this:
-----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: DES-EDE3-CBC,444D0046AC26EA44 mutr2fuoADA/TNTw+sCEgW/ZH3G58MgKFCTKGMeaZQkEKB8113 wLn2UOfK...WTXqviLMMIaQcXF1ePqR2HfB1VVUCEm5rtDDvo 8ohaXgjUZBYZTmPmdIPEUtC+5gzVqUird3a6bDozsuo= -----END RSA PRIVATE KEY-----
If you encrypt the key with any other algorithm, for example AES 192 with CBC, then you would see the "cannot instantiate private key". For example, the GenerateJWT policy will not be able to de-serialize this valid private key:
-----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: AES-128-CBC,F7B406D39C87775A25514DF40E8573FF bj9VS0lti6hMmeKPJGr39xaloKAlEmpIFcxbvr+kDMChLQAywkbHwlM/eO7sYYwI 31VkrD8MK07tLoGekv3rrvRKgZ0i1a5xEUP2EhU8qOpgbJm9CR9DFn6 .... w99aav0Yc4QaRsJFNXIwDyWWSyHqdRDuQPljHneFkpx8ap2cHWgEdNcc -----END RSA PRIVATE KEY-----
This problem has been noted (b/79526748) and fixed, but the patch has not yet been released. The workaround: use a non-encrypted private key or use a DES3-encrypted private key.
There are other potential causes of "cannot instantiate private key". For example:
- you didn't pass a valid PEM-encoded private key
- the key is encrypted with DES3, but the password is incorrect
- There is some other formatting that is amiss
Whether you are experiencing any of these is hard to say. I'd need to look at the policy configuration, and the private key string.
Just in case it needs to be said: If you post the private key string, be sure to mask out most of the base64-encoded data. The private key is a secret; don't post it in its entirety here. I would need to see the top of the PEM file in each case, but not the full payload.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Dino Sorry for late response, we found why it is failing.
we were generating the private key using following command,
"openssl genrsa -out private-encrypted-rsa-des.pem 2048" -This doesn't show the algorithm in private key.
pic.1
But when we use the following command,
"openssl genrsa -des3 -out private-encrypted-rsa-des3.pem 2048" -This show's the algorithm in private key.
pic.2
By using the private key(in pic.2) we were able to successfully generate & validate the JWT token.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, thanks for the reply. I'm glad it's working for you.
We're working on making this more tolerant of the various PEM formats. Improvements are coming so that you will be able to use the old RSA format, encrypted keys, unencrypted keys, and new formats for both. Much more flexible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please share the commands ran to generate the keys and get the tokens generated / verified
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ask a new question please. When you ask, you'll want to provide more than 8 words describing what you want. A short phrase like "please share the commands to generate the keys and tokens" is not enough context to explain what you are trying to do, what you have tried, and what you are stuck on.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,661 -
API Security
174 -
Apigee General
3,021 -
Apigee X
1,263 -
Developer Portal
1,906 -
Drupal Portal
43 -
Hybrid
459 -
Integrated Developer Portal
87 -
Integration
308 -
PAYG
13 -
Private Cloud Deployment
1,067 -
User Interface
75
| User | Count |
|---|---|
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter