- Google Cloud
- Cloud Forums
- Apigee
- Apigee edge saas ssllabs Qualys B Rating -Logjam a...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
We have seen the Qualys SSL report for Apigee by providing virtual host alias as a server name, covering all Tesco endpoints exposed via Apigee. It shows Apigee only has a B rated because it is subject to weak Diffie-Hellman key exchange parameters leading to Logjam attack, CVE-2015-4000
Ciphers do not order by strength, resulting in lower strength ciphers being used when both the server and client support a higher strength cipher. Too many ciphers listed which impacts performance due to the size of data transferred during TLS handshake.
Attached screenshot ciphers-list.png
How to address this issue?
Thanks In Advance
Nandeesha
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
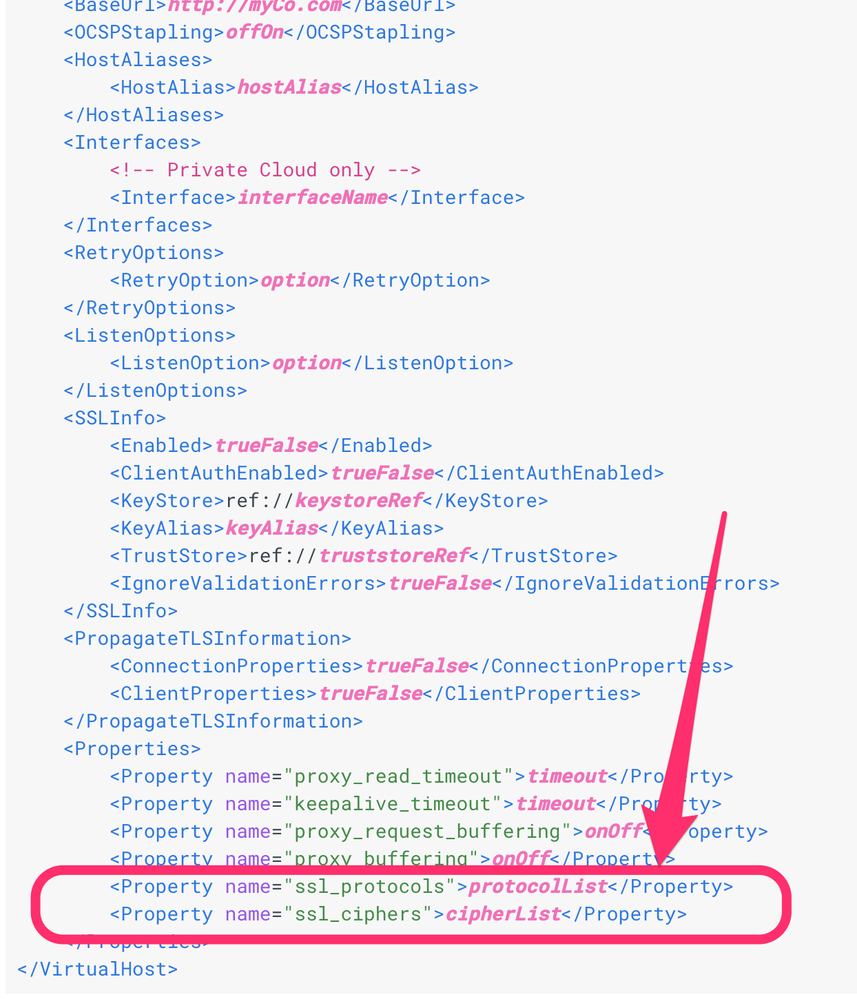
It sounds to me that your vhost is supporting ciphers and maybe protocols you don't want it to support.
In that case, restrict the ciphers and protocols using the appropriate properties on the vhost. You didn't show your vhost configuration, so I'm guessing you didn't restrict things at all.
See the doc here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It sounds to me that your vhost is supporting ciphers and maybe protocols you don't want it to support.
In that case, restrict the ciphers and protocols using the appropriate properties on the vhost. You didn't show your vhost configuration, so I'm guessing you didn't restrict things at all.
See the doc here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, Dino
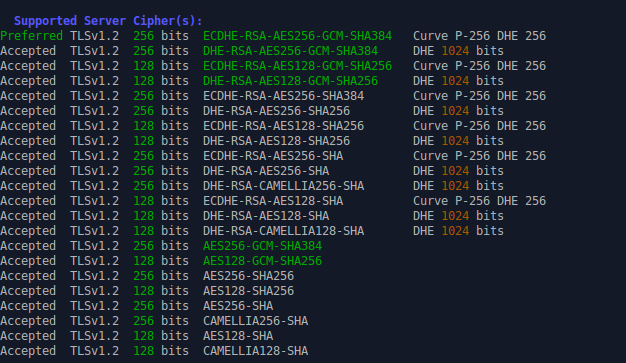
I have performed a sslscan to list out supported ciphers on the virtual host and noted the DHE 1024 bits(Weak Cipher) attached the screenshot below.
SSLLabs scan will downgrade our results and has “B” rated because it is subject to weak Diffie-Hellman key exchange parameters leading to Logjam attack, CVE-2015-4000
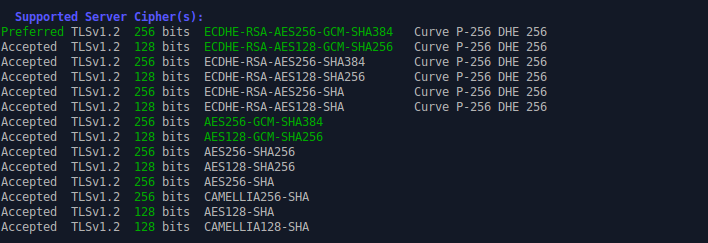
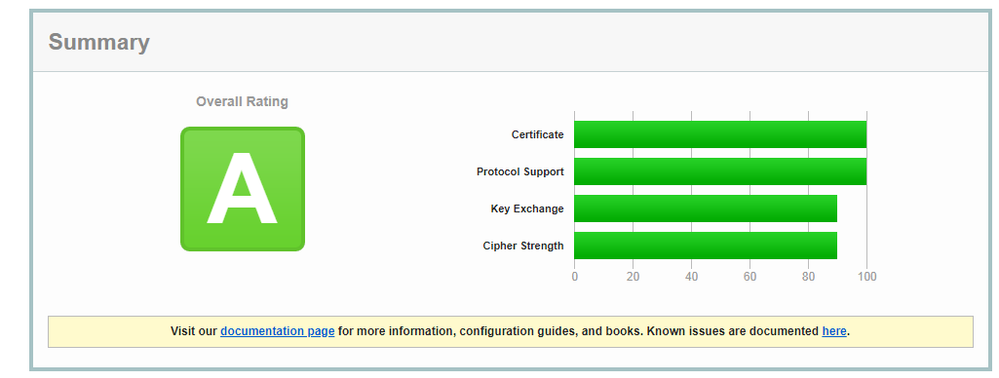
As you suggested, I have done a POC on this in a test environment. I restrict the ciphers on the vhost along with !DHE and rescanned with SSLLabs this time it was rated “A” and attached screenshot as shown in the below.
<strong><Propertyname="ssl_ciphers">HIGH:!aNULL:!MD5:!DH+3DES:!kEDH:!DHE</Property></strong>
If I restrict DHE ciphers on a virtual host level, client connection will not happen(fail) for those clients rely on below DHE ciphers.
DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-CAMELLIA256-SHA: DHE-RSA-AES128-SHA:DHE-RSA-CAMELLIA128-SHA
Do I need to raise a support ticket with apigee to consider adding support for 2048-bit DHE or stronger Diffie-Hellman groups as suggested in Logjam attack, CVE-2015-4000 and the below reference link
https://weakdh.org/sysadmin.html
Reagrds
Nandeesha
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Nandeesha,
Yes, contact Apigee support. Your plan sounds right . I agree that by default, Apigee should not expose endpoints that allow the weaker DH ciphers that are vulnerable to the Logjam (and other) attacks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Dino,
I have opened a case with apigee regarding this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is what I learned: By some time last year, almost all of the Apigee-hosted virtual hosts had been updated to remove support for DHE ciphers with weak keys.
Some customers, apparently you are in that group, had specifically requested to continue to support weak DHE because there are some bonafide clients that depend on this weaker security. For those, Apigee did not update the routers to eliminate the weak DHE. This was done as a compatibility measure, but we recommend that customers remove weak DHE as soon as is possible.
Customers that want to correct this on their vhosts should contact Apigee Support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Planning to work on same Related issue, Hoping Apigee Support will be with me!
Thanks In Advance 🙂
-
Analytics
497 -
API Hub
75 -
API Runtime
11,660 -
API Security
174 -
Apigee General
3,020 -
Apigee X
1,262 -
Developer Portal
1,906 -
Drupal Portal
43 -
Hybrid
459 -
Integrated Developer Portal
87 -
Integration
308 -
PAYG
13 -
Private Cloud Deployment
1,067 -
User Interface
75
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 1 | |
| 1 |

 Twitter
Twitter