- Google Cloud
- Cloud Forums
- Apigee
- Genarate JWT Token :- Read KVM for privatekey
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
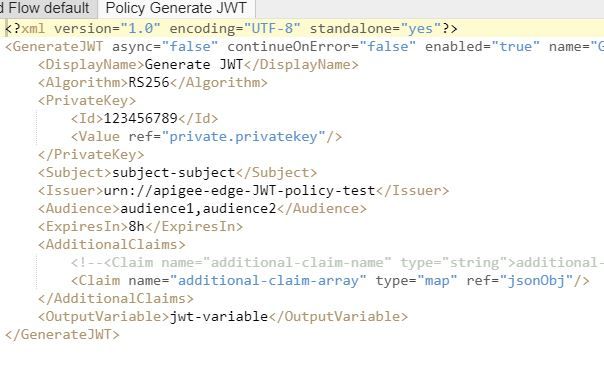
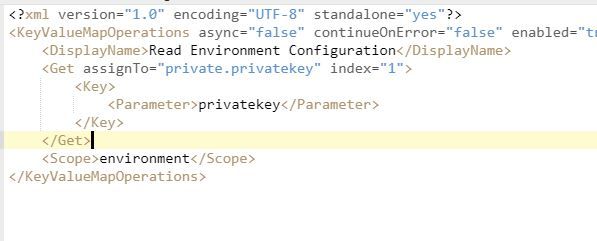
I want to genarate JWT token and I've kept privateKey in KVM but when I use GenerateJWT policy it throws an error. Details are as mentioned below;
KVM :-
{ "encrypted": true, "entry": [{ "name": "privateid", "value": "123456789" }, { "name": "privatekey", "value": "U2lkZGhlVGVzdGluZw==" } ], "name": "JWTTestConfiguration" }
Error Message :- cannot instantiate private key
Below are the screen shots of the policies
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @siddhesh.malvankar1, this is a known issue. Today, it's not possible to load a multi-lined value like the contents of a PEM file, into the KVM using the Apigee Edge administrative user interface. There's a bug in handling newlines in the textarea (reference b/64808634).
More info here,
https://community.apigee.com/articles/57541/how-to-retrieve-keys-for-jwt-from-kvm.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe you need to remove the index="1" from the KVM policy.
This
<KeyValueMapOperations name='KVM-GetPrivateKey' mapIdentifier='secrets'>
<Scope>environment</Scope>
<ExpiryTimeInSecs>15</ExpiryTimeInSecs>
<Get assignTo='private.privatekey'>
<Key>
<Parameter>key1</Parameter>
</Key>
</Get>
</KeyValueMapOperations>
And not this:
<KeyValueMapOperations name='KVM-GetPrivateKey' mapIdentifier='secrets'>
<Scope>environment</Scope>
<ExpiryTimeInSecs>15</ExpiryTimeInSecs>
<Get assignTo='private.privatekey' index='1'> <<<< NO
<Key>
<Parameter>key1</Parameter>
</Key>
</Get>
</KeyValueMapOperations>
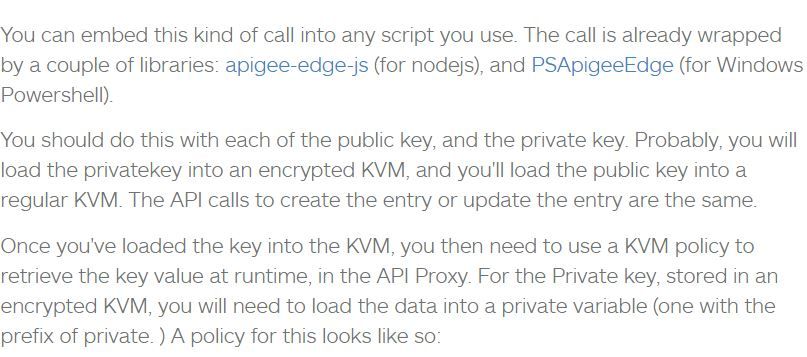
This repo shows you how to load private keys from the encrypted KVM. It includes a set of sample proxies. The one you want is jwt-generate. Look at the proxy flow; some of the JWT generation uses a key set with AssignMessage. Some use a key retrieved via KVM Get. There is also a command-line tool to load a private key into .a KVM. Siddharth is correct that the KVM UI is broken and doesn't handle lengthy values elegantly. But it's a matter of display; the command line tool will load in the key nicely.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @siddhesh.malvankar1, this is a known issue. Today, it's not possible to load a multi-lined value like the contents of a PEM file, into the KVM using the Apigee Edge administrative user interface. There's a bug in handling newlines in the textarea (reference b/64808634).
More info here,
https://community.apigee.com/articles/57541/how-to-retrieve-keys-for-jwt-from-kvm.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Articles suggest that we can upload KVM values using JavaScript. But I'm still unable to upload it, Could you please suggest what should I do if I want PrivateKey in key value maps.
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I haven't tried Dino's approach. But for testing purpose, you can use an Assign Message policy to Assing a private.key variable with the certificate in the value.
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<AssignMessage async="false" continueOnError="false" enabled="true" name="Assign-privatekey">
<DisplayName>Assign-privatekey</DisplayName>
<Properties/>
<AssignVariable>
<Name>private.privateKey</Name>
<Value>
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,1BFD44A98CAAF56A
nprtxjYSl8bGYc0B15ZWxDa5XvCPuQx+OaTT9o1wtlq1QxUNfm8yCHwxq+n7KgBm
CAgAZ11M3f+NlMS76+yZOeKzf55y7332IqsEZIjZpN2OXb6lg1ICM3D0UcN3lHdk
AsC4bBPddFCNmYcWpPXtXRQyaTraNep6tjRItj8gsaTaZEYPLY6Yes1SuBNGlSkL
w8s2dWyTY/wxfsyW1LJtYscLnh7XIHqv03JakUgpSsl2PDzxsEHFgC01BtG2WpWM
/D+h4i/Q/oa6VosEke48IgJQSvCwGvqc0QAE5TQv7c2oZURbZbS1MXKILFsfak9Q
3CML9P+HveQ+MahJwjlwNEVZRmjTOyfFsthSRxZwhYpxxfsqHLjnYLHCBRhtLg5i
b6MLbwXpOTuYwvPVfxEI5lT6ZdHnxhspjQoV95SQebj+5NZf2xhO3jNIgORTM5AM
n9a4s3HnLoo1thN2lAuoZymWLMITVQbw4jElfcFMHog3sssIpKS/tMgeKtMs6Yxf
jhMhac2IOPDVx5v/6y9eDnQlCimLSm5uDNV4+m/sOso2Zh6YFUp6ByPoK1x9Hv5h
kewOI70d/p22iOhW/YzVktNwUcYk548tsUCdWXYjTxzSKG2RZhNMvCggQRUM3qoH
9tlMVBjIHzH5Mh+ko6WugCOfN22x0uvl2YAnkgT7oCWZ0a1ZK9iVDb1kSjjpFu+1
M0t0D4oqeVtnmA+9RQYV4TahadJtj71v+EjKJtRh+CpJeYwRSE6uSv8zlHwcR/Y5
nWReJBs0cSGWYJPXqw2yYTVZv7Rzdw/h0A5HK7MCkHFf/BRqbrVMaeFYJuPHwZOH
svnqyHpnkHgfCAwBXhcLHQLh4uZC1LF4Qfs6y8fb/mEQMFZRakut7yBdzh9dHt1a
tuN64iXydn+kyzbBIcLxCIs4cS9QfUvWtXwS0w9eidx4cqs02046SZC6uYV1agxF
2MEG4i1FCyRXJLOQpa0WcWrHzPMGLBpCPHe0NgDm1hgSj7HLkLuYkEL4WAcZ5gPU
60pa6og1WolmLgqYOH+blypB/gxRSxFB0cCir/09S7ppd9FX8n1pQSt8D22xZ6is
42hR4Fu4JBQaxCBunkgaAU/ozwE/fEstTB+BdPuid8wsCTtd9QyHJ60ZjYTm2dF0
+0nED8Oj5N3dcAX8YHZWBo+DT2+n7WcViTR3Q1tNG4bjE1+krJyYcGSeLFWcxaZp
+Zh6/bxV/+oV2uM2Q0tWZaoyTwz65iQ1QeTZzqj3vEVM8peXZDVFb6AA8buu6jFq
4/pAe4RqUH0zumnXBnDmW/fDUPSIbHCCn+aeqNDOTVYtzWiwZegHmcGR3mc+brfv
Pa3MGXsMQPhqHW+tVSc6jn8sxCaFS5vYkweDUTNZMfoCLG9ajQOMQksicv+pTLrH
uKIfciKPYAgBM4IG1Q9TG+7LR2DMCnbg0fuzrqldX/07DsdVX270JphLAidsqTNq
+1xaZOXvSn7mnHW8Syjf5dK2dBSbhp8WCTVOj4B+huKhS+qcnxSMyS2QjVh1Qpq1
cxPb0DpiPJ49ZNwW5x+GpB71W0rCAuk19/ZIIeTg7rqvc/tOwd0kFAoCAcfyjYYf
-----END RSA PRIVATE KEY-----
</Value>
<Ref/>
</AssignVariable>
<IgnoreUnresolvedVariables>true</IgnoreUnresolvedVariables>
<AssignTo createNew="false" transport="http" type="request"/>
</AssignMessage>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe you need to remove the index="1" from the KVM policy.
This
<KeyValueMapOperations name='KVM-GetPrivateKey' mapIdentifier='secrets'>
<Scope>environment</Scope>
<ExpiryTimeInSecs>15</ExpiryTimeInSecs>
<Get assignTo='private.privatekey'>
<Key>
<Parameter>key1</Parameter>
</Key>
</Get>
</KeyValueMapOperations>
And not this:
<KeyValueMapOperations name='KVM-GetPrivateKey' mapIdentifier='secrets'>
<Scope>environment</Scope>
<ExpiryTimeInSecs>15</ExpiryTimeInSecs>
<Get assignTo='private.privatekey' index='1'> <<<< NO
<Key>
<Parameter>key1</Parameter>
</Key>
</Get>
</KeyValueMapOperations>
This repo shows you how to load private keys from the encrypted KVM. It includes a set of sample proxies. The one you want is jwt-generate. Look at the proxy flow; some of the JWT generation uses a key set with AssignMessage. Some use a key retrieved via KVM Get. There is also a command-line tool to load a private key into .a KVM. Siddharth is correct that the KVM UI is broken and doesn't handle lengthy values elegantly. But it's a matter of display; the command line tool will load in the key nicely.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI @Dino-at-Google,
Thanks for reply, one more query regarding the JWT. Now I can successfully generate the token using KVM but as my need I want to verify same token in C# code and I've written below program but it's failing to validate. Any suggestion on it. I've attached the code file for your reference.programcs.txt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the error you are getting in C#?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We can add multiline KVM using directly through Environment configuration user interface which converts it into single line value.
Thanks @Siddharth Barahalikar and @Dino-at-Google 🙂
-
Analytics
497 -
API Hub
75 -
API Runtime
11,661 -
API Security
174 -
Apigee General
3,021 -
Apigee X
1,263 -
Developer Portal
1,906 -
Drupal Portal
43 -
Hybrid
459 -
Integrated Developer Portal
87 -
Integration
308 -
PAYG
13 -
Private Cloud Deployment
1,067 -
User Interface
75
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter