- Google Cloud
- Cloud Forums
- Apigee
- Oauth2 with OpenId connect in Apigee
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, I am asking you today because I am at a dead end. I have missed piece in the logic of Oauth2 and OpenID connect in apigee.
I understand that an application request Openid connect to have the profile of the loggedin user and that OAuth2 offers a way for an application to access a protected resource via an access token.
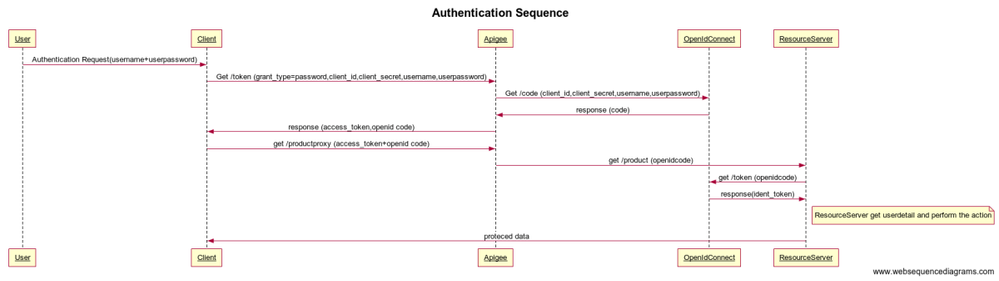
Now we take a scenario where a protected resource needs to verify that the logged in user is himself that has taken the authorization token, is this illustration that I have done here is good or I make things complicated?
- Labels:
-
API Runtime
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Adouani Riadh, I think you are talking about PKCE, which is described in IETF RFC 7636.
I have written a post on the topic, please have a look & we can discuss,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello and thank you for your answer.
Sorry, I think my situation is some kind different that explained in the document.
In fact, I have an API that serves files based on the identity of the user so Oauth2's access token is not enough for me to authorize client to get the data.
Consider the scenario that a client application asks apigee for a token using Resource password grant mechanism, and Apigee allows it. My API cannot serve this client until it knows the identity of a real user.
I cannot associate the email (userID) with OAuth2 access token when I call "/ product", because the client application can request my API with the same Token and different emails and will have an unauthorized access to protected data.
So, my API must determine the identity of the person before serving the data so that it can serve the right user
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You and I have a different understanding of how OAuthV2 works.
The Password grant allows the OAuth token dispensary to authenticate the user with a password; a correctly behaving token dispensary will issue a token via password grant_type only if the user is authentic. Normally if you use Apigee Edge to dispense the token, you would configure the token dispensing flow to:
- authenticate the user via an external Identity Provider (IdP)
- using the response from the IdP, attach some custom metadata (like an email address, or even a set of roles belonging to the user) to the token as a custom attribute during generation.
You wrote:
I cannot associate the email (userID) with OAuth2 access token when I call "/ product", ...
I disagree. In fact, you CAN associate an email with a token. Everyone who is using Apigee Edge correctly, does this. This is normal, standard, best practice for tokens issued via password grant.
Suppose Apigee Edge has issued a token via password grant, and has associated an email address and role to the token, as described above. Now imagine a subsequent request that presents the token back to Apigee Edge. The API proxy calls OAuthV2/VerifyAccessToken , and that implicitly loads into the request context, the metadata associated to the token including the custom attributes (like email or role) that were attached to the token during generation.
At that point you could configure your API Proxy to take conditional action based on the email or role, etc.
...the client application can request my API with the same Token and different emails and will have an unauthorized access to protected data.
No. When using tokens generated via password grant, the client does not send in a token along with an email address, and an assertion that the token is usable for that email address. The client sends only the token. The Apigee Edge server validates the token, and loads the metadata persistently associated to that token. For a token issued by password grant, the email address is stored as metadata for the token, at the token store. The client cannot tell the Apigee Edge server that the token belongs to a different email address than the email address stored with the token by Apigee Edge.
Also, for tokens generated via password grant, the client is TRUSTED. This is because the client itself handles user credentials. A malicious client could store those creds and replay them at any time to obtain new tokens on behalf of the user, and then perform arbitrary actions. Therefore we assume that the client participating in a password grant is trusted. As a corollary of that Trust, we assume that the client uses tokens correctly - does not covertly store them and replay them later, without user consent.
By the way: If you do not trust the client to handle user credentials, for example if it is a third-party client, then you would use authorization_code grant_type.
In the end, the client obtains and handles the token; the client must be trusted to NOT re-use that token in a context that is not on behalf of the user.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Dino , I figure out how I will do it based on your tutorial about oidc in apigee. I will implement openid connect in apigee to handle user identity rather than add metdata to oauth token. I missundertood oauth 2 and openid connect the first time when I post my question but after that I figure out that openid connect is based over oauth and beside handles authorization, it handles user identity and authentification
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dino , I am trying to understand your example on OIDC Tutorial. I have followed all the given steps and running login app locally and when call APIGEE and while the request redirected to login page but i am seeing this error ..
37| <div>
38| <input type="hidden" id='sessionid' name='sessionid' value="<%= txid %>" />
>> 39| <input type="hidden" id='oidcserver' name='oidcserver' value="<%= oidcserver %>" />
40| <input type="hidden" id='client_id' name='client_id' value="<%= client_id %>" />
41| <input type="hidden" id='response_type' name='response_type' value="<%= response_type %>" />
42| <input type="hidden" id='requestedScopes' name='requestedScopes' value="<%= req_scope %>" />
oidcserver is not defined
where do i configure OIDC Server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
please ask a new question, rather than posting a question in a comment to an old answer.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,661 -
API Security
174 -
Apigee General
3,021 -
Apigee X
1,263 -
Developer Portal
1,906 -
Drupal Portal
43 -
Hybrid
459 -
Integrated Developer Portal
87 -
Integration
308 -
PAYG
13 -
Private Cloud Deployment
1,067 -
User Interface
75
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter