- Google Cloud
- Cloud Forums
- Apigee
- CI problem: how to set up accounts for continuous ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
we have an interesting conundrum that I havnt been able to hack out yet. Please note that this is for a private cloud installation – but for anyone who is interested in providing CI services to a public cloud instance – you might want to watch this space!
Currently – we have created policy groups w/ specific sets of permissions for users of the UI and the Management API.
Generally we are running under the following assumptions:
1)We have an organization that might contain many different classes of users who would have access only to the proxies, products, and applications that they create.
2)Nobody who is in these various groups is an org admin by design
3)Each of these groups has the ability to CREATE proxies, CREATE products, and CREATE apps
4)We have demonstrated that most of the time when a user in one of these groups creates a proxy or a product in the UI, they are automatically granted control over the app in the ui. There are some exceptions to this which we are trying to pin down as they cause mayhem in the organization –(but this isnt the point of this post!)
Here is the problem: when a permissioned user uses node tool to create a proxy or product their group is NOT granted control over the proxy or product they are creating. They are unable to follow up a create with an edit. They are unable to log into the UI and fix things. It takes the intervention of an ORG admin to assign the correct permissions.
So does anyone have a solution to this problem that does not include granting Org Admin permissions to accounts performing CI activities?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Benjamin,
This sounds like a user role configuration problem. The user account for your CI may not have sufficient permissions.
Please see our documentation on roles here and feel free to let me know if you have any questions. It might just take a small tweak to your CI user to get things working as you want.
EDIT: tl;dr for comment thread below: There is a bug in Apigeetool where a newly created API proxy does not automatically get added to custom role for EDITing. This is different from the UI where doing the same creates proper permissions in the custom role for the new API proxy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Benjamin Goldman , How do you list proxies ? Using Management API / apigee-tool ? What exactly do you mean "another user will have to show up and make this modification defeating the whole purpose." Can you please provide more details to understand better ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Anil Sagar- I will update the question with more specifics. I suspect that there is either a but in on-prem 15.04.03, or that the RBAC (which seemed to go through some changes recently) were modified w/o respect for some fine details in the create functionality which a user or application would expect.
I just wont be able to until later today.. full day 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Benjamin Goldman - you certainly have an interesting continuous integration process if someone needs to go after CI's deployment and make modifications...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One would say that we have an interesting potential bug in how the RBAC works which is forcing us to do that 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Benjamin,
This sounds like a user role configuration problem. The user account for your CI may not have sufficient permissions.
Please see our documentation on roles here and feel free to let me know if you have any questions. It might just take a small tweak to your CI user to get things working as you want.
EDIT: tl;dr for comment thread below: There is a bug in Apigeetool where a newly created API proxy does not automatically get added to custom role for EDITing. This is different from the UI where doing the same creates proper permissions in the custom role for the new API proxy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Alex - i hate to say it - but yeah - we know that 🙂 The problem is that there is an all-or-nothing approach to this which seems to be different in on-prem 15.04.03 than it was in 15.01. I will update the question with more details - but this reply doesnt actually answer my question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Benjamin,
Sorry, I could only give the best answer based on the question you asked and details you provided.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No problem: when i finally get an answer that is usable or gives me the real situation ill be awarding points for everyone that tried!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect you are running into a bug between a proxy created in nodetool and proper permissions for other users in that role.
Could you please try this test? If you create the bundle via the UI, not using the nodetool, then other users in the same role should be edit the bundle. It's a work-around, but that may be the fastest work-around in the meanwhile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can do that - but i cant offer that work around to our internal customers. They are pretty tough customers and are currently evaluating the ability of Apigee to allow CI functionality. If i could get away with it i would just grant them ORG ADMIN - but i cant get away with it :( is this something I should raise to support then?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No need to raise to support just yet-- I'd like to run a few more test on my end. If you have the opportunity and can try the test as I proposed on your end, that will also help expedite a fix.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hopefully later today.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried both with the user role and a custom role, and I had no issue with creating an API with Apigeetool followed by editing the proxy with another user in that same role. I think you meant that you also have permissions to EDIT all proxies-- without EDIT permission, I can't deploy using Apigeetool.
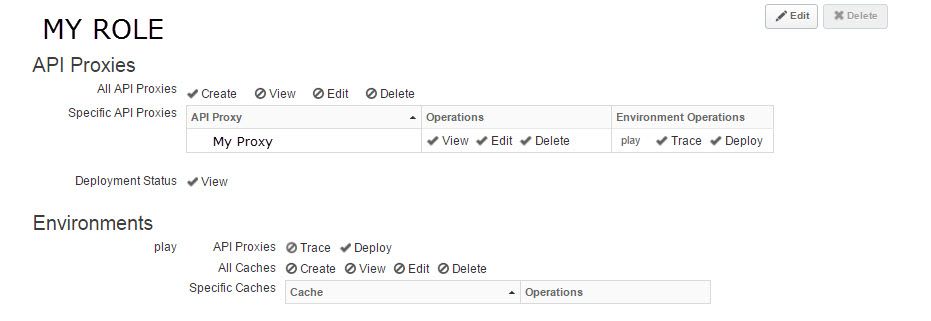
Can you confirm the permissions on API proxies? Or even better, can you send a screenshot of the permissions on your custom role so we can replicate?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
if I log in as a user in this role - i can create a proxy using the UI and it gets added to the list of managed proxies (im skipping the whole bit about products for the moment)
if I use an account in this role from the node tool the proxy created does not seem to be getting into this list - we have had to log in and add the permissions manually.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Got it. I confirmed the behavior you describe. I'll file a bug on our end. If you need urgency on this fix, please open a support ticket and have them reference me (Alex Koo).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ill probably do that. In the mean time im going to grant higher perms and just keep my fingers crossed 😞
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Alex Koo So i just successfully created a proxy w/o edit rights. It did not deploy to the specified environment though. I havnt checked what the stack trace i got back means (not really going to have time to). When I add edit back to "all" this is not a problem anymore. This means that a proxy created is NOT getting assigned the correct permissions. (which I also confirmed!)
This isnt really a good work around because it would allow team 1 to overwrite team 2's proxies. Defeats the purpose of having the different permissions.
This is definately a bug. Should I open a bug report now? As "non critical" as this is - its got a bunch of really technical people here up in arms because they cant do something they would expect to be able to simply...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
as soon as i get to a machine that can do anything on the network i will 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is going to have to wait until tomorrow. I must sleep 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@arghya das we need more help here... is this something you can help with or could include who could?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Birute Awasthi i just added a comment below and it actually edited a comment made by Alex and overwrote his...and now I have edit rights on his stuff on this page...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Alex Koo funny thing - i tried to open this as a support issue in case 919537 - but was told that its NOT a bug with edge but with the node tool.
Personally I feel that this is not correct - creating a proxy should cover this use case on its own based on the account that created it.
Not really sure what to do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No disagreement here-- it is a bug with the apigee node tool, not with Edge. I've already filed a bug a while back (APIRT-2121). But please keep in mind that apigeetool is an open source project with very different SLAs than Edge UI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You think so? I thought it was the other way around. Create should work w/o any special features.. i dont see how it could otherwise...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just want to make sure I understand your concerns. Per your original post, you wrote this:
"Here is the problem: when a permissioned user uses node tool to create a proxy or product their group is NOT granted control over the proxy or product they are creating."
This is the same behavior we are observing, and you stated this is a problem (undesirable behavior). I am agreeing that the node tool's behavior to 'create a proxy that the created user's group is NOT granted control over the proxy or product they are creating' is a bug. This behavior is not observed in Edge.
Are you now saying you think Edge's behavior is incorrect while node tool's behavior is correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Benjamin Goldman, I see that our Support team is helping you with this. We can continue discussions through the Support case if you have further concern.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,660 -
API Security
174 -
Apigee General
3,020 -
Apigee X
1,262 -
Developer Portal
1,906 -
Drupal Portal
43 -
Hybrid
459 -
Integrated Developer Portal
87 -
Integration
308 -
PAYG
13 -
Private Cloud Deployment
1,067 -
User Interface
75
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 1 | |
| 1 |

 Twitter
Twitter