- Google Cloud
- Articles & Information
- Cloud Product Articles
- RBAC with Fine Grained Access - Apigee X
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Background
Many customers have asked for fine-grained access to develop API Proxies and Shared Flows that allows development teams to work privately and to control access to specific environments. This solution guide provides a step-by-step solution that works nicely for both Apigee APIs and in the Apigee management console.
See also RBAC with Fine Grained Access - Apigee X - Using Groups.
User Story
As a security stakeholder, I want to restrict access to Apigee resources so that I can assign them to separate business units or projects.
- Business unit leads should be able to grant user access to their own environment(s).
- Business unit members should only be able to access Apigee resources that belong to the business unit. These resources should include:
- Development resources:
- API Proxy
- Shared Flow
- Deployments
- Debug Sessions
- Flow Hooks
- Developer resources:
- API Products
- Rate Plans (see Limitations and Caveats)
- App Developers (see Limitations and Caveats)
- Applications (see Limitations and Caveats)
- Environment resources: (see Environment Access)
- KVMs
- Resource files
- TargetServers
- References
- KeyStores
- Development resources:
Overview
Supported Resource Types
Apigee supports adding resource conditions in IAM policies to these supported resources types using conditional role bindings during role assignment. Conditions can be based on time (e.g. schedule, expiry) or a named resource (e.g. type and name starts with “bu1-”). Roles can be assigned to individual users or to a group.
TIP: Assigning conditional access to a group simplifies management as once the conditions have been specified for the group, individual users are simply added to the group. This avoids updating the conditions on every user assignment.
NOTE: This guide uses a single user role assignment in a project, but the steps are similar when using a group in an organization.
Environment Access
Environments do not support conditional role assignment directly. Rather, access to an environment and its resources is granted via “Access” in the UI or via the Apigee API Environments Set IAM Policy API. Assigning a user as an “Apigee Environment Admin” to an environment (e.g. bu1-test) controls access to environment specific resources such as KVMs, Resource files, TargetServers, References, and KeyStores. It also controls access to deployments and debug sessions for the environment.
Unsupported Resource Types
These resource types do not support “conditional” role based assignment, access to these resources can be managed via built in roles or custom roles.
- Analytics Dashboards
- Custom Reports
- Advanced API Security
- Advanced API Ops
- Integrated Developer Portals
- Integrations
- Connectors
Limitations and Caveats
- Rate Plans
- Rate Plans are associated with an API Product, therefore access can be protected by the API Product name.
- Rate Plans are identified using a UUID; it’s not demonstrated how to apply conditional role assignment.
- App Developers
- Developers are identified using either an email or a UUID; it’s not demonstrated how to apply conditional role assignment.
- Applications
- Although Applications can be restricted by name, The “Apps” list page in the UI performs a “GET /apps?expand=true” API call which returns all the details for an App thereby allowing the user to see any App’s keys.
Overview of Steps
Using GCP IAM Console or GCP APIs:
- Assign Apigee API Admin and Apigee Developer Admin roles to user or group with conditions on role assignment.
- Create and assign a custom role “Custom Role Apigee Deploy and Debug” with get and list permissions for environments and deployments, to users without conditions. This fixes UI errors preventing deployments and debug sessions.
Using Apigee UI or Apigee APIs:
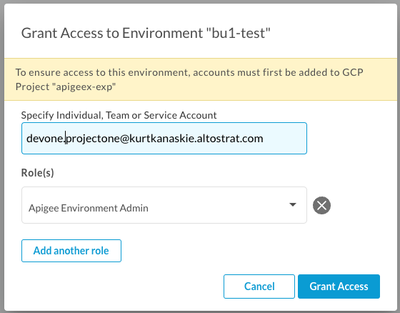
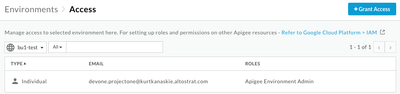
- Assign Apigee Environment Admin “Access” for the user to specific Environments (e.g. bu1-test).
Solution Details
Apigee supports adding resource conditions in IAM policies on specific resource types (proxies, shared flows) used in the Apigee builtin rules through GCP IAM. Not all resource types are “conditional”, in particular Environments. Access to environments is done via “Access” in the UI or via the Apigee API Environments Set IAM Policy API. Assigning a user as an “Apigee Environment Admin” to an environment (e.g. bu1-test) controls access to environment specific resources such as KVMs, Resource files, TargetServers, References, and KeyStores.
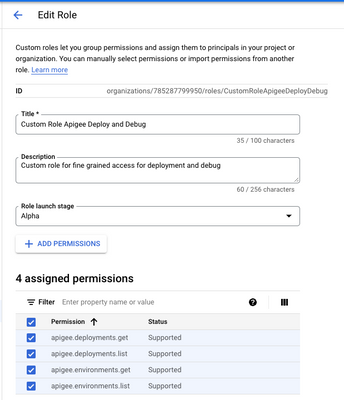
Create Custom Role
This is required to allow the user to manage deployments and debug sessions in the Apigee UI. It also enables configuring Flow Hooks, for the assigned environment.
Create a custom role (e.g. Custom Role Apigee Deploy and Debug) that allows get and list permissions on deployments and environments.
apigee.deployments.get
apigee.deployments.list
apigee.environments.get
apigee.environments.list
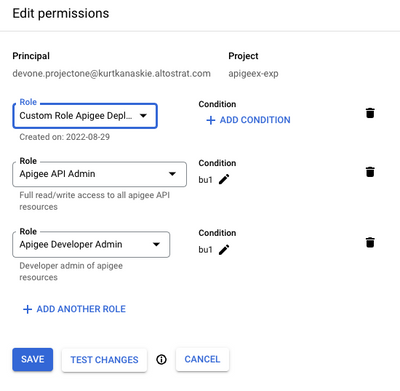
Assign Roles
The Apigee built in roles for Apigee API Admin and Apigee Developer Admin are required for an “API proxy developer” to create and test proxies and shared flows. Apigee API Admin role is required to create API proxies, shared flows and related artifacts such as API Products. Apigee Developer Admin role is required to create Developers and Apps for testing.
Assign Conditions to Assigned Roles
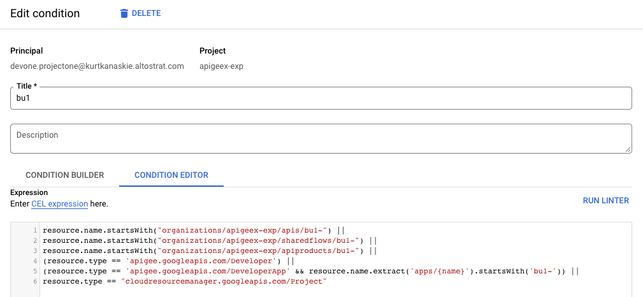
Add the following conditions to both the Apigee API Admin and Apigee Developer Admin role assignments.
- The use of (resource.type == 'apigee.googleapis.com/Developer') allows users to list Developers and their Apps.
- The use of (resource.type == 'apigee.googleapis.com/DeveloperApp' && resource.name.extract('/apps/{name}').startsWith('bu1-')) allows access to named Developer Apps.
NOTE: the resource.name.startsWith() condition uses the name of the project (e.g. apigeex-exp).
resource.name.startsWith("organizations/apigeex-exp/apis/bu1-") ||
resource.name.startsWith("organizations/apigeex-exp/sharedflows/bu1-") ||
resource.name.startsWith("organizations/apigeex-exp/apiproducts/bu1-") ||
(resource.type == 'apigee.googleapis.com/Developer') ||
(resource.type == 'apigee.googleapis.com/DeveloperApp' && resource.name.extract('/apps/{name}').startsWith('bu1-')) ||
resource.type == "cloudresourcemanager.googleapis.com/Project"
- Navigate to IAM & Admin → IAM in the GCP Console
- Add a principal and assign Apigee API Admin role.
- Click the pencil to “Edit principal”
- Click the pencil to add the Condition
Select “CONDITION EDITOR” and paste the condition from above, adjusting “bu1-” to be your resource prefix.
Repeat for the Apigee Developer Admin role.
The final role assignment for the user:
Assign User Access to Environment
Access for users to specific environments is done in Apigee UI or via APIs on the environment. Access to environments is required to allow management of environment specific resources such as Target Servers, KVMs and PropertySets, since these are not named resources and cannot be used in conditional role assignments. Access to environments is also required to manage deployments for the specific environment.
Role assignment in the Apigee Management UI
References
GCP IAM and Roles
Apigee Users and Roles
- Users and Roles Overview
- Add user accounts in the UI
- Adding resource conditions
- Complete list of Apigee API REST resources.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for writing this up. This helps to start addressing the lack of built-in access control in Apigee, which has been a pain point for us. I followed your steps to test it on my end and wanted to share some feedback when I logged into our org as a test user with the assigned conditional roles:
- The UI lists all proxies and shared flows in the org, but if I click on one I don't have access to, I get a message like "Can't get revision list for sharedflow foobar: Missing revision list from ListApiProxyRevisions call." This is a little confusing since it's obfuscating a permission denied/forbidden error. If I close the error the page just continues to endlessly load.
- Clicking on an API product from the list of all products does nothing at the UI level, but when looking at the network logs in my browser, I can see the API call returning an error. It just seems the error isn't presented at the UI level.
- Adding a condition to the Develop App is problematic, since that is a resource created by our API consumers. We can't expect someone to namespace their application name in the developer portal. This is especially tricky if someone creates an application registering to multiple API products, where the API products are owned by different API publisher groups/teams.
Otherwise, I think the solution here is a great temporary workaround until a more native solution is released in Apigee.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I agree, it's not 100% and there are some UI "subtleties".
Good point regarding Apps, I just wanted to show what I learned about "resource.name.extract".
BTW, there's another article showing this using groups.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @kurtkanaskie, thanks for your article, this was very helpful in managing users at an organisational level.
At environmental level I already assigned custom roles to groups of users . Do you know if by using API calls or apigeecli commands we will also be able to restrict access to specific KVMs or target servers?
I would like to apply conditions also for environmental resources.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @sebastiank,
KVMs, target servers and other environment specific resources are not "named" resources and cannot use conditional role assignment. Best you can do is to assign "Access" for a user or group to the environment.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @kurtkanaskie,
I have applied the condition for ApiProducts and Developers. But all the products are accessible on UI. The condition on IAM doesn't seen to work. Please let me know what can cause this issue.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @nswapna,
I just re-tested this and it works on my organization. I have 2 products "bu1-product-1" and "bu2-product-1". A user that is assigned conditions for "resource.name.startsWith(\"organizations/apigeex-exp/apiproducts/bu1-\")" is only able to access a product that begins with "bu1-". They can see all the products in the list, but cannot access anything besides "bu1-" prefixed products.
Make sure you have only assigned roles "Apigee API Admin" and "Apigee Developer Admin" with conditions, along with the "Custom Role Apigee X Deploy and Debug" without conditions in GCP IAM.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Can i create an IAM condition to control access to Developer portal ?
Say, i want user 'A' to be allowed to created pages/menu only with artifact starting with 'A'
similarly, user 'B' to be allowed to created pages/menu only with artifact starting with 'B'
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
IAM conditions are not supported for the Integrated Portal.
See docs:

 Twitter
Twitter