- Google Cloud
- Articles & Information
- Cloud Product Articles
- Assigning Custom Roles for Environment based RBAC ...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Question: How do I create a custom role and assign it to an user for only a given Environment in Apigee X or hybrid Orgs?
Answer:
I get asked this question a lot and hence decided to post a community article about this. In this post we will start with a little background of RBAC on Google Cloud, do a brief solution overview and then walk-through an example scenario for creating "custom" Environment Admins on a per Environment basis.
Background:
Access control in Apigee X / hybrid is controlled by Google Cloud Identity and Access Management (Cloud IAM). Cloud IAM lets you set permissions specifying who has what kind of access to which resources in your project. For more information, see Concepts related to identity.
Users are a type of member, a broad term that refers to an identity that can be granted access to resources. Other types of Cloud members include service accounts, Google groups, and Google Workspace domains. For more information, see this overview of Cloud Identity and Access Management.
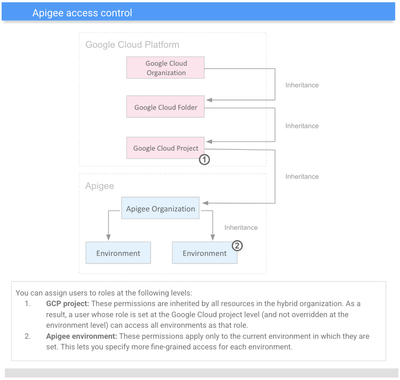
Since our original question talks about environment specific access, it will be good to do a quick read on role inheritance within Apigee, as we will be using this concept later in this article.
Overview:
Broadly speaking there are two parts to solving for the above requirement, part one is granting limited access to Apigee X or hybrid org (for basic access to Org scoped resources like org, proxy etc.) and part two is granting more permissive RBAC access using another custom role at the environment level. Please refer to our public docs for more information on Apigee access control.
Apigee X and hybrid both use the GCP IAM for Role Based Access Control (RBAC), hence we will be using the GCP IAM Console for creating our custom roles and granting the Org level access (part one). And since “Environment” is an Apigee specific construct, the granular access for admin access to an environment (part two) will be set up within Apigee X / hybrid itself. We will be using our community supported tool apigeecli to accomplish part two.
Example Scenario:
Lets walk through an example to see how we may go about achieving this. Say we have two envs (dev, eval) in our ORG and we would like to assign a custom Environment Admin role to an user on our dev environment only.
Prerequisite:
We will be creating 2 separate custom roles for controlling access to Org and Environment based resources. Here is a link to IAM Documentation for overview on creating custom roles.
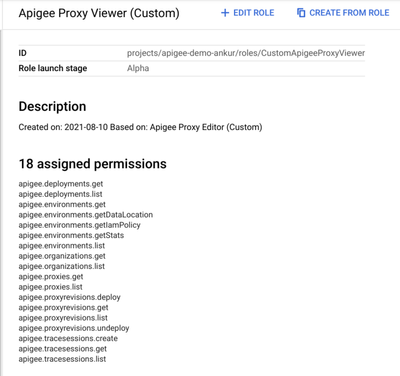
- Create Org Access Custom Role - This role will grant basic access to Org scoped resources like org, proxy etc. Using the GCP IAM Console create a custom role (CustomApigeeProxyViewer) with the following 18 permissions: (see screenshot)
Note- These permissions can be fine tuned as per your requirements. As an alternative you could also have used the Apigee API Reader Standard profile here, I am using a custom role for illustrating customization.
Note- These permissions can be fine tuned as per your requirements.
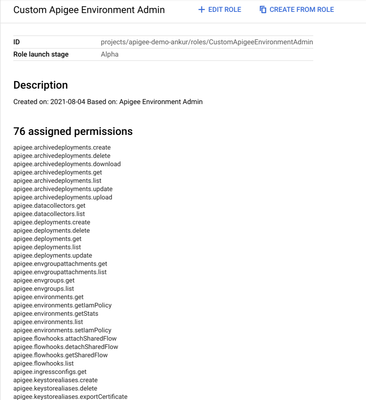
- Create Environment Access Custom Role - This role grants admins access to an individual environment. We can clone the standard environment admin role (CustomApigeeEnvironmentAdmin) and fine tune the permissions based on our custom needs. See below for example role I have created:
Solution:
Now let's assign these Custom Roles to our User:
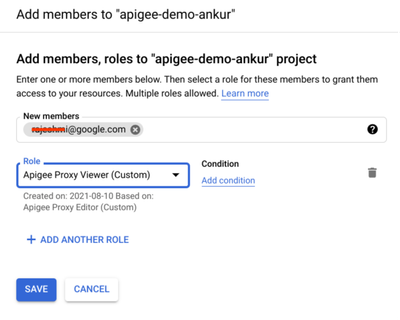
Part one - Use GCP IAM to assign the custom role - CustomApigeeProxyViewer to our user
Part Two - Assigning of Environment based access is done within the Apigee X / hybrid Management plane. Currently the UI does not support this capability so we will use the setIamPolicy Apigee API endpoint to accomplish this. Alternatively, we can use our community supported tool apigeecli. It enables us to interact with Apigee APIs using a command line interface (cli) approach.
Steps to assign Custom Environment Access Role to User via API (using apigeecli)
- Get the latest apigee CLI version (v1.100 is the latest version of this cli atm)Note - you can follow installation instructions on the github repo for Mac and Windows based hosts, the command below are for linux terminals.
wget https://github.com/srinandan/apigeecli/releases/download/v1.100/apigeecli_v1.100_Linux_x86_64.zip - Unzip and Add the current directory to path and setup token, ORG and ENV environment variables
unzip apigeecli_v1.100_Linux_x86_64.zip export PATH=$PATH:./apigeecli_v1.100_Linux_x86_64 export ORG=<Your Apigee Org name> export ENV=<Environment name> i.e. dev token=$(gcloud auth print-access-token) - Using the apigeecli to assign the CustomApigeeEnvionmentAdmin role to the user
apigeecli envs iam setcustom -n <username>@google.com -m user -r projects/$ORG/roles/CustomApigeeEnvironmentAdmin -e $ENV -t $tokenPro Tip: - The apigeecli tool is self documenting and you can use the --help option to get more info on what parameters to provide for a specific operation. For example :
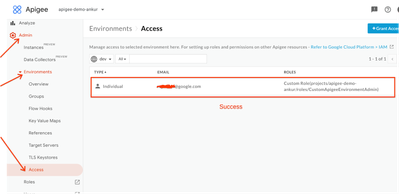
apigeecli envs iam setcustom --help - Using Apigee UI you can now verify that the user above has been added to the Environment with the custom role based access. You can either navigate to this UI endpoint by using UI menu - “Admin - > Environments -> Access” or simply replace org and env name in this URL and paste this in your browser
https://apigee.google.com/organizations/<org name>/environments/<env name>/access - You can also ask the user to login to Apigee and verify that they have “Admin” access to the “dev” environment only.
Summary:
We saw how we can create separate org and environment level custom roles and assign these to a user for granting more permissive environment level access to a given environment.
Clean-up:
We can revoke the association of the user with the environment based access using the same apigeecli tool we used to grant this access. Here is an example command:
apigeecli envs iam removerole -r projects/$org/roles/CustomApigeeEnvironmentAdmin -m user -e $env -n user@google.com -t $token
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
thanks for this.
Are there any guidelines how to map it to organization RBAC being done in IDP such as Azure AD / Okta etc.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I got error when running this:
apigeecli envs iam setcustom -n <username>@google.com -m user -r projects/$ORG/roles/CustomApigeeEnvironmentAdmin -e $ENV -t $tokenThe solution was to add --org $ORG. then it works.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@shuklaankur @welylauCan you help me with this doubts, please. I realized the same configuration with a "Evaluation Account Apigee X" , but the configuration roles not take for enviroment in Apigee Access. Can be for i used "Evaluation
Account Apigee X"?. Steps of my configuration:
1. Set basic role "Viewer" in IAM GCP
2. Create custom role with permision "Apigee Developer"
3. Set IAM policy with this role "Apigee Developer" only "dev" enviroment (i have 2 enviroments dev/qa).
In my configuration, Must i have the same role in IAM GCP and Apigee access or another configuration that i am forget?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @AlvaroRALA,
You typically set Environment Admin via "Access" to the environment, not Apigee Developer. Doing that controls access to anything associated to the environment such as Target Servers, Deployments and Debug Sessions.
You may find this article useful: https://www.googlecloudcommunity.com/gc/Cloud-Product-Articles/RBAC-with-Fine-Grained-Access-Apigee-...

 Twitter
Twitter