- Google Cloud
- Articles & Information
- Cloud Product Articles
- ApigeeX proxy chaining across environments
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
| tl;dr A proxy chaining solution for ApigeeX to chain calls across environments within an org by leveraging Apigee provided runtime IP address and peered DNS setup. |
Proxy chaining in ApigeeX using LocalTargetConnection only works within the same environment.

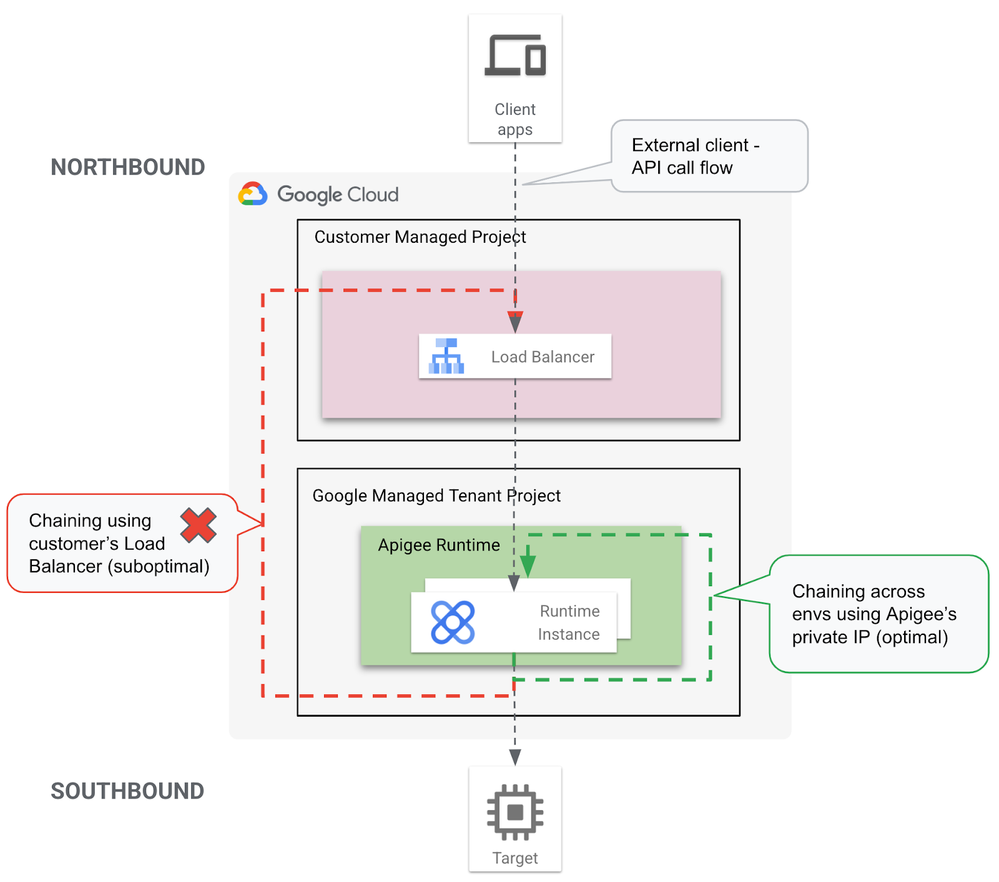
Using DNS peering, a private DNS entry is made in a customer’s project to allow the use of a hostname to reach Apigee’s northbound private IP address.
|
🛑 IMPORTANT To access the child proxy with this solution, you can only use a subdomain of the form To use a custom domain name an external load balancer is required and hence negates the benefits of this solution. |
Note: For a standalone demo you can start with the Terraform sample x-dns-peering that takes care of the DNS peering step.
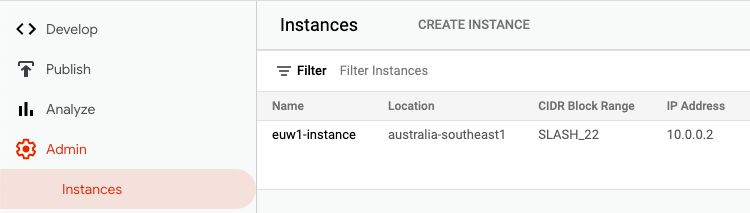
Get runtime IP address
From ApigeeX, find the private IP address of Apigee runtime from Instances.
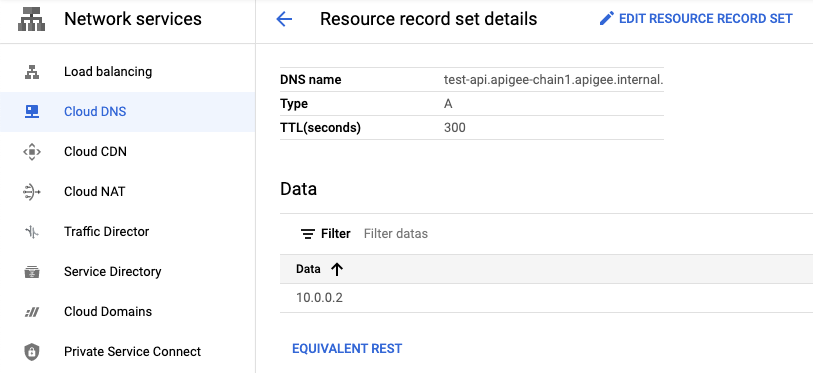
Configure Private DNS
In Cloud Console, create peered DNS and create a private DNS - A record
<sub-domain>.<apigee-org>.apigee.internal -> <private-IP>
Example:
test-api.apigee-chain1.apigee.internal -> 10.0.0.2
Screenshot of the DNS entry in GCP Network services
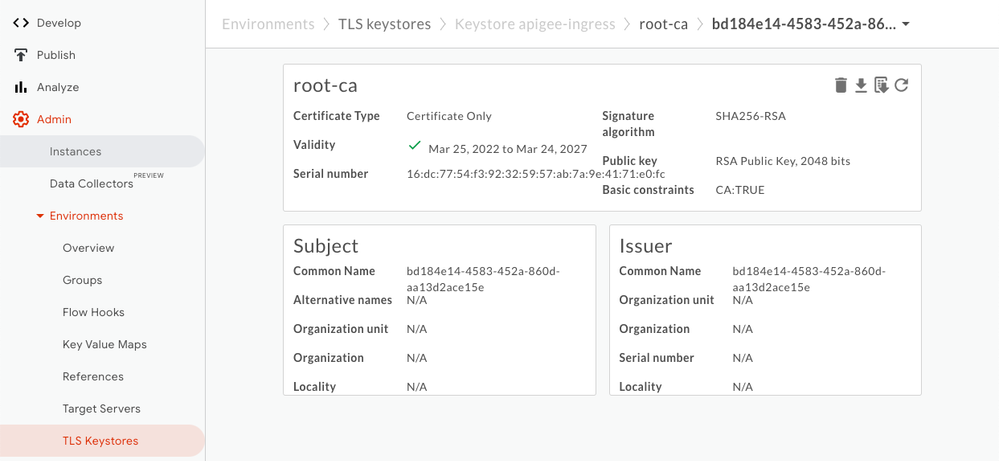
Get Apigee org certificate
Using curl or your favorite REST client, call organizations API to get Apigee Org details.
GET https://apigee.googleapis.com/v1/organizations/{apigee-org-name}From the response, extract the value of “caCertificate” attribute, base64 decode and save as a .pem file (to use in the Truststore step below)
curl -H "Authorization: Bearer $(gcloud auth print-access-token)" \
https://apigee.googleapis.com/v1/organizations/myenterprise-org | \
base64 --decode > apigee-cert.pemCreate Truststore (TLS Keystore)
In ApigeeX, add org public certificate from earlier step (apigee-cert.pem file) to trust store (TLS Keystore) and name it "apigee-ingress" for example.
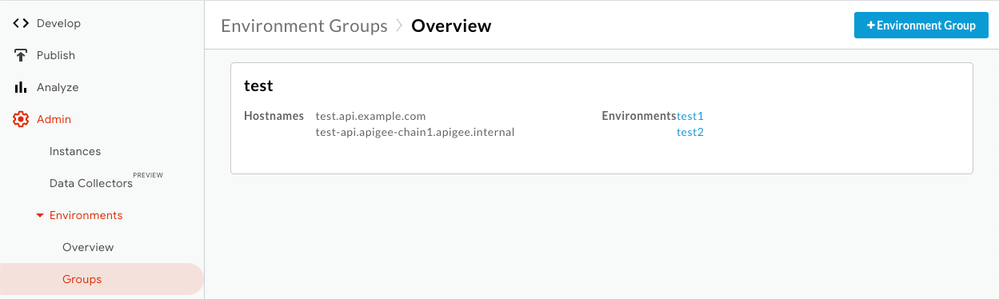
Environment Group
In ApigeeX, add the following hostname to the desired environment group.
<sub-domain>.<apigee-org>.apigee.internalExample: test-api.apigee-chain1.apigee.internal
Target Endpoint
In ApigeeX, parent proxy’s TargetEndpoint, use truststore and point to the child proxy using the earlier configured hostname. “/hello-world” is the basepath of the child proxy.
Note: There is no need to use additional HTTP header like “host” or the need to skip TLS validation.
<HTTPTargetConnection>
<SSLInfo>
<Enabled>true</Enabled>
<TrustStore>ref://apigee-ingress</TrustStore>
</SSLInfo>
<URL>https://test-api.apigee-chain1.apigee.internal/hello-world</URL>
</HTTPTargetConnection>Testing
To test, invoke curl as follows. The flag "-k" is required as curl does not use the self-signed server certificate. ApigeeX however uses the certificate and hence does not ignore TLS errors.
curl -k https://test-api.apigee-chain1.apigee.internal/parent-proxy
 Twitter
Twitter