- Google Cloud
- Cloud Forums
- Apigee
- Mask passwords with JSONPath issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I'm adding to the organization level a mask for passwords. The xml looks like this:
<MaskDataConfiguration name="default">
<JSONPathsRequest>
<JSONPathRequest>$..password.</JSONPathRequest>
<JSONPathRequest>$..oldPassword.</JSONPathRequest>
<JSONPathRequest>$..newPassword.</JSONPathRequest>
</JSONPathsRequest>
<JSONPathsResponse>
<JSONPathResponse>$..password.</JSONPathResponse>
<JSONPathResponse>$..oldPassword.</JSONPathResponse>
<JSONPathResponse>$..newPassword.</JSONPathResponse>
</JSONPathsResponse>
<Variables>
<Variable>ServiceCallout.request</Variable>
<Variable>request.formparam.password</Variable>
</Variables>
</MaskDataConfiguration>
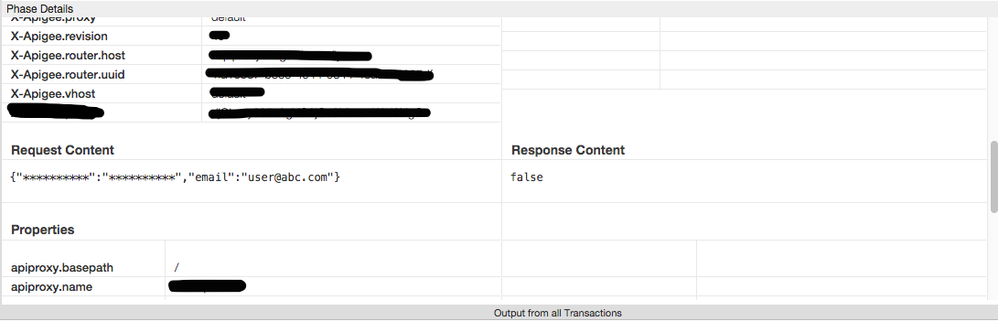
Using that description for the mask I noticed that if you have a json request that looks like this
{ "email": "user@abc.com", "password": "password"}
on the Edge I see this
{ "email": "user@abc.com", "**********":"**********"}which is quite easy to infer the password 🙂
So, is that an expected behavior on the Edge or is it a bug?
Thanks,
Matias
- Labels:
-
API Runtime
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
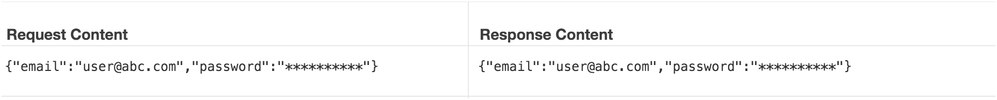
@Matias It might appear that there's a correlation between the actual and the masked characters in terms of the total number of characters and what the actual content could be, but that's not true. You can try with a very long string and it would still mask it the same way.
But I do see your point about the key getting masked, which can act as some sort of indication of what the value could be. This is a known bug, that we are already aware of and should get fixed in some future release. Here's a sample request, where the masking happens differently:
curl -v http://myapis.apigee.net/masking -d '{ "email": "user@abc.com", "password": "unknownpasswordstring"}' -H "content-type: application/json"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Matias I would also like to confirm, if you are a trying this on cloud or on-premises. If I remember correctly, this bug was fixed on our cloud release somewhere in October and I see its working fine. If you are on some version of OPDK, you might need a patch for this fix. If you can share more details about your test environment, it would be great.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@arghya das Thanks for the information.
We are working with the on-premises version 4.15.07.00
Is there a patch available for this issue?
Thanks,
Matias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Matias I would have to look it up. Even if there's not one, you can always request for it since the next major version is not out yet. I will check the status of that bug and see if its packaged in any of our patches on 1507 and let you know.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,664 -
API Security
175 -
Apigee General
3,030 -
Apigee X
1,275 -
Developer Portal
1,907 -
Drupal Portal
43 -
Hybrid
461 -
Integrated Developer Portal
87 -
Integration
309 -
PAYG
13 -
Private Cloud Deployment
1,068 -
User Interface
75
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter