- Google Cloud
- Cloud Forums
- Apigee
- Limit Proxy Endpoints when Using Target Server vs ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right now we are proxying a REST svc. Let's say the target service lives at https://my.host.com and has an endpoint mapped to uri path of /baz. Let's say that target host also has other services mapped to uri path /internalUseStuff that we do NOT wish to proxy.
Now let's say my api proxy uses a base path of /foo/bar, and that per apigee doc recommendations, we are using a target server configs by env to decouple target server URLs. So we have a target server called my-target which maps to https://my.host.com.
So, with all the above mappings in play, a request to https://<apigee host>:<apigee secure port>/foo/bar/baz will properly map to
BUT, https://<apigee host>:<apigee secure port>/foo/bar/internalUseStuff would also be passed through as https://my.host.com/internalUseStuff, since target server only includes host name and port.
IF we do the target endpoint config by URL, I can make both proxy endpoint and target endpoint include the /baz so that ONLY /baz is accessible, NOT /internalUseStuff.
BUT since we want to use the target server to decouple concrete URLs that vary by env from our proxy config, we can't include /baz in the base path of the proxy endpoint b/c we need it to be tacked on to the host name referenced by the target server, along with any additional uri path and query arms from the request.
Sorry for the long setup, but I wanted to be very specific and precise about our situation and why it's configured the way it is. So...when using a target server to decouple env-specific URLs from proxy config, how do we appropriately allow only /baz through but not /internalUseStuff ? we could get crazy with javascript and/or reg ex stuff, but that seems like overkill. It seems like there should be a way to do this much more simply in how we map base path and target server, but trying to add /baz to base path and to target server host name doesn't work (the latter expects host only, not URI pathing).
Thanks in advance!
- Labels:
-
API Runtime
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Patrick McMichael Thanks for posting this question to the community.
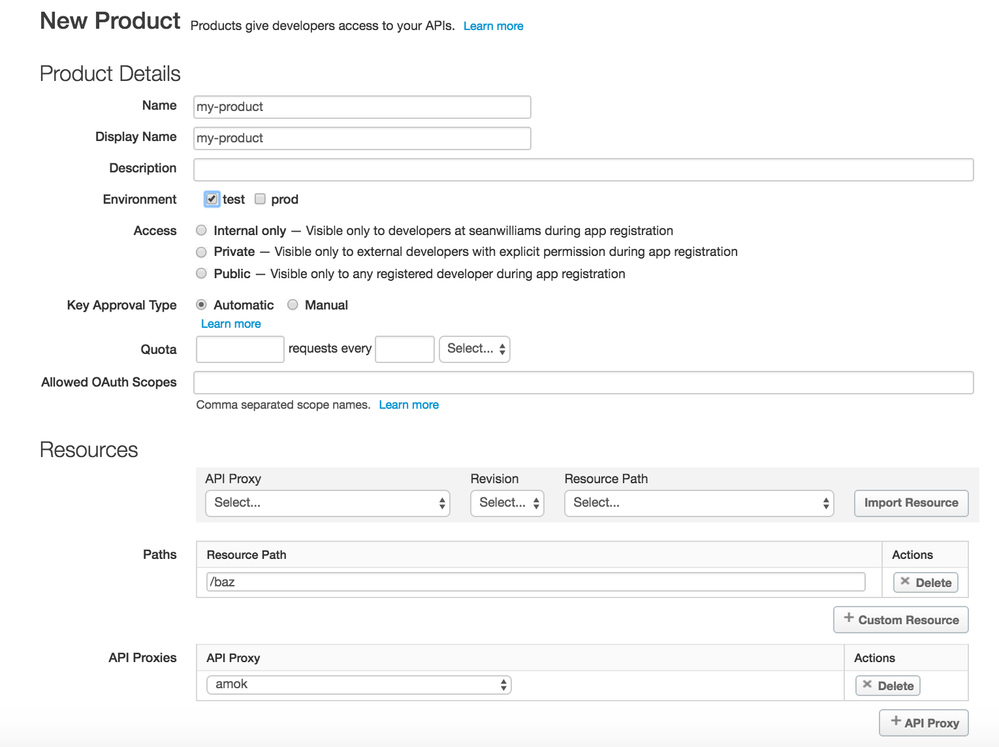
I think the solution to your question is to use Apigee products, so I'm assuming that you are protecting your API with OAuth 2.0. If you setup an Apigee product, then you can configure the resource path that is available from your product. So in the screen shot below, I added the resource path of /baz and I selected the proxy that includes that resource. This will make sure that only /baz is available to developer apps that consume this product. As I mentioned earlier, this setup assumes that you are using OAuth 2.0 to protect your resources.
If you need help configuring OAuth 2.0 you can try this tutorial to start, which describes how to configure the API product, Developer App and Developer. It also describes the policies that should be added to your proxy to protect it with API key validation.
http://docs.apigee.com/tutorials/secure-calls-your-api-through-api-key-validation
The following tutorial will describe how to protect it with OAuth 2.0.
http://docs.apigee.com/tutorials/secure-calls-your-api-through-oauth-20-client-credentials
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Normally this would be handled in the proxy endpoint, where you can filter by path and verb. For example:
<ProxyEndpoint name="default">
<Description/>
<Flows>
<Flow name='flow 1'>
<Description>insert description here</Description>
<Request>
<!-- insert flow-specific policies here -->
</Request>
<Response>
<!-- and others here -->
</Response>
<Condition>(proxy.pathsuffix MatchesPath "/baz") and (request.verb = "GET")</Condition>
</Flow>
<Flow name='unknown request'>
<Request>
<!-- throw a fault if none of the above flows match -->
<Step><Name>RF-UnknownRequest</Name></Step>
</Request>
<Response/>
</Flow>
</Flows>
<PreFlow name="PreFlow">
<Request/>
<Response/>
</PreFlow>
<HTTPProxyConnection>
<BasePath>/foo/bar</BasePath>
<VirtualHost>secure</VirtualHost>
</HTTPProxyConnection>
<RouteRule name="default">
<TargetEndpoint>default</TargetEndpoint>
</RouteRule>
<PostFlow name="PostFlow">
<Request/>
<Response/>
</PostFlow>
</ProxyEndpoint>
The above would accept GET /foo/bar/baz , but raise a fault for any other verb or path.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great point @Dino. This approach will deny all requests to /internalusestuff across all Apps. If you want to grant specific apps access to the /internalusestuff path, then you should use the product approach I outlined above and also create a Conditional Flow for the /internalusestuff path.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,664 -
API Security
177 -
Apigee General
3,037 -
Apigee X
1,283 -
Developer Portal
1,909 -
Drupal Portal
43 -
Hybrid
463 -
Integrated Developer Portal
89 -
Integration
309 -
PAYG
13 -
Private Cloud Deployment
1,068 -
User Interface
76
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter