- Google Cloud
- Cloud Forums
- Apigee
- JWT verification failing in Apigee for azure b2C t...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi google ,
@dchiesa1
I am retrieving JWT from azure b2c .
I can get a public key from azure and verify the signature in jwt.io using the public key .
However , if I use Verify JWT Policy in apigee it is failing with Invalid token: policy(Verify-JWT-Azure-B2C) and error.class com.apigee.steps.jwt.verify.VerificationException.
Assign message policy content from proxy setting the Public Key :
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<AssignMessage async="false" continueOnError="false" enabled="true" name="AM-JWKS">
<DisplayName>AM-JWKS</DisplayName>
<Properties/>
<AssignVariable>
<Name>azure.publickey</Name>
<Value>-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAtVKUtcx/n9rt5afY/2WF
NvU6PlFMggCatsZ3l4RjKxH0jgdLq6CScb0P3ZGXYbPzXvmmLiWZizpb+h0qup5j
znOvOr+Dhw9908584BSgC83YacjWNqEK3urxhyE2jWjwRm2N95WGgb5mzE5XmZIv
kvyXnn7X8dvgFPF5QwIngGsDG8LyHuJWlaDhr/EPLMW4wHvH0zZCuRMARIJmmqiM
y3VD4ftq4nS5s8vJL0pVSrkuNojtokp84AtkADCDU/BUhrc2sIgfnvZ03koCQRoZ
mWiHu86SuJZYkDFstVTVSR0hiXudFlfQ2rOhPlpObmku68lXw+7V+P7jwrQRFfQV
XwIDAQAB
-----END PUBLIC KEY-----</Value>
</AssignVariable>
<IgnoreUnresolvedVariables>true</IgnoreUnresolvedVariables>
<AssignTo createNew="false" transport="http" type="request"/>
</AssignMessage>
Verify Jwt Policy content :
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<VerifyJWT async="false" continueOnError="false" enabled="true" name="Verify-JWT-Azure-B2C">
<DisplayName>Verify JWT-Azure-B2C</DisplayName>
<Algorithm>RS256</Algorithm>
<Source>id_token</Source>
<PublicKey>
<Value ref="azure.publickey"/>
</PublicKey>
</VerifyJWT>
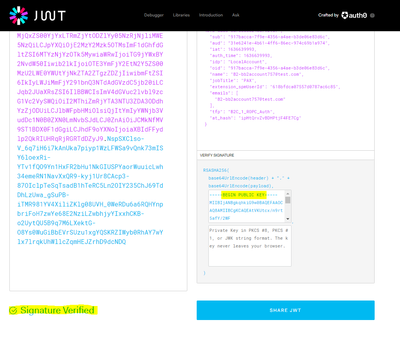
id_token: "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6Ilg1ZVhrNHh5b2pORnVtMWtsMll0djhkbE5QNC1jNTdkTzZRR1RWQndhTmsifQ.eyJleHAiOjE2MzY2NDc1NTAsIm5iZiI6MTYzNjY0Mzk1MCwidmVyIjoiMS4wIiwiaXNzIjoiaHR0cHM6Ly9zaXRhc3BtLmIyY2xvZ2luLmNvbS9kMDE1OTQ4Ni04YmFkLTQzNzMtOGFjNi04YTdjMDgwYzI0ODgvdjIuMC8iLCJzdWIiOiI5MTdiYWNjYS03ZjllLTQzNTYtYTRhZS1iM2RlMDZlODNkNmMiLCJhdWQiOiIzMWU2MjQxZS00YjYxLTRmZjYtODZlYy05NzRjNjliMWE5NzQiLCJpYXQiOjE2MzY2NDM5NTAsImF1dGhfdGltZSI6MTYzNjY0Mzk1MCwiaWRwIjoiTG9jYWxBY2NvdW50Iiwib2lkIjoiOTE3YmFjY2EtN2Y5ZS00MzU2LWE0YWUtYjNkZTA2ZTgzZDZjIiwibmFtZSI6IkIyLWJiMmFjY291bnQ3NTdAdGVzdC5jb20iLCJqb2JUaXRsZSI6IlBBWCIsImV4dGVuc2lvbl9zcG1Vc2VySWQiOiI2MThiZmRjYTA3NTU3ZDA3ODdhYzZjODUiLCJlbWFpbHMiOlsiQjItYmIyYWNjb3VudDc1N0B0ZXN0LmNvbSJdLCJ0ZnAiOiJCMkNfMV9ST1BDX0F1dGgiLCJhdF9oYXNoIjoiZGVLT3NwWEliWHV1UFZ4ak9ZYW9BUSJ9.pcbt3BW4debZ57MJ0mbITI4vmHvRsSSe9FOnAnjGF1x_E2eP1fexL2ITjxyBHsNc-Dc9wBY51oFA6a5HsaezCblO6MNPCBwBxR0eOBe_OjPOMgh50AUqln1xYAIRC-Dwe72Ob46vnYmwNeXxe0tLaRuiCj0hNjY_QQ7PiTfh29LhKdV36FAar34b_OeJ6SVMwitlkDTheSmhxCt722V16CN7VKmMS1AB6ah_c1P7kSR-DQUVgDuDncNs6cTl2cc5eIpCnFLKuOvT22HskbRlj0zX0yxXaobROEW-aQ0fkbS0wfBcDgjeihSLvsUuCjETtoMq2rbtP8hQFijgCLkMtQ"
Can you please help debug the issue .
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @dchiesa1
You are correct the value being verified was not clean string .
THe azure b2c token response actually returns multiple values in response :
"access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6Ilg1ZVhrNHh5b2pORnVtMWtsMll0djhkbE5QNC1jNTdkTzZRR1RWQndhTmsifQ.eyJpc3MiOiJodHRwczovL3NpdGFzcG0uYjJjbG9naW4uY29tL2QwMTU5NDg2LThiYWQtNDM3My04YWM2LThhN2MwODBjMjQ4OC92Mi4wLyIsImV4cCI6MTYzNjYzMzg4MCwibmJmIjoxNjM2NjMwMjgwLCJhdWQiOiIzMWU2MjQxZS00YjYxLTRmZjYtODZlYy05NzRjNjliMWE5NzQiLCJpZHAiOiJMb2NhbEFjY291bnQiLCJvaWQiOiI5MTdiYWNjYS03ZjllLTQzNTYtYTRhZS1iM2RlMDZlODNkNmMiLCJzdWIiOiI5MTdiYWNjYS03ZjllLTQzNTYtYTRhZS1iM2RlMDZlODNkNmMiLCJuYW1lIjoiQjItYmIyYWNjb3VudDc1N0B0ZXN0LmNvbSIsImpvYlRpdGxlIjoiUEFYIiwiZXh0ZW5zaW9uX3NwbVVzZXJJZCI6IjYxOGJmZGNhMDc1NTdkMDc4N2FjNmM4NSIsImVtYWlscyI6WyJCMi1iYjJhY2NvdW50NzU3QHRlc3QuY29tIl0sInRmcCI6IkIyQ18xX1JPUENfQXV0aCIsImF6cCI6IjMxZTYyNDFlLTRiNjEtNGZmNi04NmVjLTk3NGM2OWIxYTk3NCIsInZlciI6IjEuMCIsImlhdCI6MTYzNjYzMDI4MH0.XobXMHQkhQlDP_70bFbkobKO1qUDzjwzWKfBhq4kNzDRoSaV9KuPexSX5dr283KHUHGPdVSqlJRRoy2863qqXY-ANGB-mO9zjYvAa7cjshlsVNSpSWE1NEqzP2TVriFjTYNA0hO5CYjxtE1ibbNjskGxji85-ZEkIJTFPVOJVsnNFQ3LmqyB-aTPfqNVgJZ_hGzLD9No2Bq_6MS1uP4Wav3pMMxnCm20NQ100yWYXfawyrvQGso11qutVUreP41cD6yExntXSNNh05HyMY5uzf6mT_n7Kcp9y7ecU7xzzRMgYncJumnJ0k1sGi80xvOk7CsIURbB3PZT1yqqhUzFoQ",
"token_type": "Bearer",
"expires_in": "3600",
"refresh_token": "eyJraWQiOiJjcGltY29yZV8wOTI1MjAxNSIsInZlciI6IjEuMCIsInppcCI6IkRlZmxhdGUiLCJzZXIiOiIxLjAifQ..KpzPokHaMLq8IlVv.9lyyhMbOKaeQW9ChLBt3eQ5JZ1Y1U26T6-AU8Y7uf4oMw1iSb1aGjFkTfEVvXwTu7RKPa6bnsyoDiajXBLui2witHmMeNV9LzX-W8uwKva_eloDh5DjWKGpc1moJxsqGlo1IIo6Kyojx348KLOpc-vEAHBJe9Orz2koV0sbQnPI_R05VJUIFIxrsH2XitA0g9Gt6yY-5OZOtSb56lZgL4tVyM5Vem2Xlb1KHvNiST9ySKGhcoP9Q_XpsysSapdp9zT3HF6yBRo7yFbbWnNKeKKssEkSDd42phi28O2sE2D0X8p1B7YG-VMmlPeMp-AmvUgQOrSKvXQ4IV3QIaFBnSmRTnnaRZCDXZGNnyi3OohYp4Y7ebvAfeilPZZD5y8Y7eIoHpRVn1BHUMbT9o4PTpgajPa1UbIGpo6xpirAWdlPubJVOaXRoNCYgS0h_SMFixbc95T8j2axZTU9xEV2I6m9AKVaHn8z3Vd6gaKyZOopTuEgeG9E_-SZc8-PB64pIFHxPHZd7Wyx8umHAX6Dl_7xlT30HE-Z4TgAyT8lalVPX3Psd_da2P80h4Zl_fcTZoF_ikiOKO0_YVZiorEkVF70RWNwPC9x2ukZPTSHrNa6QuPv1M5BQ9tZSM6dbJ7ekP9f6Zx2-gxAYNJ3tIEkihnnto0WWr-eChHSbzZQPthG4k_qoQkYFKLYCNegJLyRJnbFfNGyKNCBnDOJqGeNIvSBw0IXbzOOXXhBsDvxAU2NM.8TNzHYd0bgPAfVF2wFf_iw",
"id_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6Ilg1ZVhrNHh5b2pORnVtMWtsMll0djhkbE5QNC1jNTdkTzZRR1RWQndhTmsifQ.eyJleHAiOjE2MzY2MzM4ODAsIm5iZiI6MTYzNjYzMDI4MCwidmVyIjoiMS4wIiwiaXNzIjoiaHR0cHM6Ly9zaXRhc3BtLmIyY2xvZ2luLmNvbS9kMDE1OTQ4Ni04YmFkLTQzNzMtOGFjNi04YTdjMDgwYzI0ODgvdjIuMC8iLCJzdWIiOiI5MTdiYWNjYS03ZjllLTQzNTYtYTRhZS1iM2RlMDZlODNkNmMiLCJhdWQiOiIzMWU2MjQxZS00YjYxLTRmZjYtODZlYy05NzRjNjliMWE5NzQiLCJpYXQiOjE2MzY2MzAyODAsImF1dGhfdGltZSI6MTYzNjYzMDI4MCwiaWRwIjoiTG9jYWxBY2NvdW50Iiwib2lkIjoiOTE3YmFjY2EtN2Y5ZS00MzU2LWE0YWUtYjNkZTA2ZTgzZDZjIiwibmFtZSI6IkIyLWJiMmFjY291bnQ3NTdAdGVzdC5jb20iLCJqb2JUaXRsZSI6IlBBWCIsImV4dGVuc2lvbl9zcG1Vc2VySWQiOiI2MThiZmRjYTA3NTU3ZDA3ODdhYzZjODUiLCJlbWFpbHMiOlsiQjItYmIyYWNjb3VudDc1N0B0ZXN0LmNvbSJdLCJ0ZnAiOiJCMkNfMV9ST1BDX0F1dGgiLCJhdF9oYXNoIjoiX1VocnNGUXJXMjh2dG5sSGF1VjdKdyJ9.JhouuYVQyJ6oLDlweJGy2YzSVDDLyW3o5XIT7-Xdm0HVUEUqKH19UvM5NUuvERMAO4iWHCMobzoV7eGVvlWJfekTu33355x_E7Ket4y4u3F5_j6_mRRFMsAmU19_-P-D9hfIbGvWgfDQ1P6zgGrfJ6_UqlSZK3aPVtmXIFNHzspEyLtIESFEjMZ8G_6AJYhdMHKBp6U-Ua1B9FTdh7H4OP6tJ_5qc5-kKWxsU1RQl4Tz2fK673e6UYvK51OG1IMUNcaxCxZdjbS7IG01mrs4NILki17NXjaeQTsot3NsQmK7X1VXLtorjGwVZjcbKseoj48GaVXWY2y9tBTJPO_xsA"
Using JS policy to extract required value set the token wrapped in quotes " " in the context variable id_token .
Removing the quotes in the assignment cleaned it up and now it is verifying as expected .
context.setVariable('id_token', JSON.stringify(azureResponse.access_token).replace('"',''));I can also verify using the published keys endpoint now which is elegant solution .
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<VerifyJWT async="false" continueOnError="false" enabled="true" name="Verify-JWT-Azure-B2C">
<DisplayName>Verify JWT-Azure-B2C</DisplayName>
<Algorithm>RS256</Algorithm>
<Source>id_token</Source>
<PublicKey>
<JWKS uri="https://sitaspm.b2clogin.com/sitaspm.onmicrosoft.com/b2c_1_signupsignin1/discovery/v2.0/keys"/>
</PublicKey>
<TimeAllowance>30s</TimeAllowance>
</VerifyJWT>
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's strange. It works for me.
This is the policy I used to set up variables:
<AssignMessage name='AM-AssignVariables'>
<IgnoreUnresolvedVariables>false</IgnoreUnresolvedVariables>
<AssignVariable>
<Name>azure.publickey</Name>
<Value>-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAtVKUtcx/n9rt5afY/2WF
NvU6PlFMggCatsZ3l4RjKxH0jgdLq6CScb0P3ZGXYbPzXvmmLiWZizpb+h0qup5j
znOvOr+Dhw9908584BSgC83YacjWNqEK3urxhyE2jWjwRm2N95WGgb5mzE5XmZIv
kvyXnn7X8dvgFPF5QwIngGsDG8LyHuJWlaDhr/EPLMW4wHvH0zZCuRMARIJmmqiM
y3VD4ftq4nS5s8vJL0pVSrkuNojtokp84AtkADCDU/BUhrc2sIgfnvZ03koCQRoZ
mWiHu86SuJZYkDFstVTVSR0hiXudFlfQ2rOhPlpObmku68lXw+7V+P7jwrQRFfQV
XwIDAQAB
-----END PUBLIC KEY-----</Value>
</AssignVariable>
<AssignVariable>
<Name>id_token</Name>
<Value>eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6Ilg1ZVhrNHh5b2pORnVtMWtsMll0djhkbE5QNC1jNTdkTzZRR1RWQndhTmsifQ.eyJleHAiOjE2MzY2NDc1NTAsIm5iZiI6MTYzNjY0Mzk1MCwidmVyIjoiMS4wIiwiaXNzIjoiaHR0cHM6Ly9zaXRhc3BtLmIyY2xvZ2luLmNvbS9kMDE1OTQ4Ni04YmFkLTQzNzMtOGFjNi04YTdjMDgwYzI0ODgvdjIuMC8iLCJzdWIiOiI5MTdiYWNjYS03ZjllLTQzNTYtYTRhZS1iM2RlMDZlODNkNmMiLCJhdWQiOiIzMWU2MjQxZS00YjYxLTRmZjYtODZlYy05NzRjNjliMWE5NzQiLCJpYXQiOjE2MzY2NDM5NTAsImF1dGhfdGltZSI6MTYzNjY0Mzk1MCwiaWRwIjoiTG9jYWxBY2NvdW50Iiwib2lkIjoiOTE3YmFjY2EtN2Y5ZS00MzU2LWE0YWUtYjNkZTA2ZTgzZDZjIiwibmFtZSI6IkIyLWJiMmFjY291bnQ3NTdAdGVzdC5jb20iLCJqb2JUaXRsZSI6IlBBWCIsImV4dGVuc2lvbl9zcG1Vc2VySWQiOiI2MThiZmRjYTA3NTU3ZDA3ODdhYzZjODUiLCJlbWFpbHMiOlsiQjItYmIyYWNjb3VudDc1N0B0ZXN0LmNvbSJdLCJ0ZnAiOiJCMkNfMV9ST1BDX0F1dGgiLCJhdF9oYXNoIjoiZGVLT3NwWEliWHV1UFZ4ak9ZYW9BUSJ9.pcbt3BW4debZ57MJ0mbITI4vmHvRsSSe9FOnAnjGF1x_E2eP1fexL2ITjxyBHsNc-Dc9wBY51oFA6a5HsaezCblO6MNPCBwBxR0eOBe_OjPOMgh50AUqln1xYAIRC-Dwe72Ob46vnYmwNeXxe0tLaRuiCj0hNjY_QQ7PiTfh29LhKdV36FAar34b_OeJ6SVMwitlkDTheSmhxCt722V16CN7VKmMS1AB6ah_c1P7kSR-DQUVgDuDncNs6cTl2cc5eIpCnFLKuOvT22HskbRlj0zX0yxXaobROEW-aQ0fkbS0wfBcDgjeihSLvsUuCjETtoMq2rbtP8hQFijgCLkMtQ</Value>
</AssignVariable>
</AssignMessage>
I used the same values you showed in your message above. And this is the policy I used to verify the JWT:
<VerifyJWT name='VerifyJWT-Azure-B2C'>
<Algorithm>RS256</Algorithm>
<Source>id_token</Source>
<IgnoreUnresolvedVariables>false</IgnoreUnresolvedVariables>
<PublicKey>
<Value ref='azure.publickey'/>
</PublicKey>
<TimeAllowance>86400s</TimeAllowance>
</VerifyJWT>
You'll see I added a TimeAllowance element there. That's to get the VerifyJWT to not throw because the JWT is expired. It says "treat it as not expired, up to 86400 seconds after actual expiry". That's one full day. You shouldn't use that kind of setting in a production system, because it basically ignores expiry. But it's useful for demonstrations, development, and diagnosis. A reasonable timeallowance in a production system might be 10-30 seconds or so.
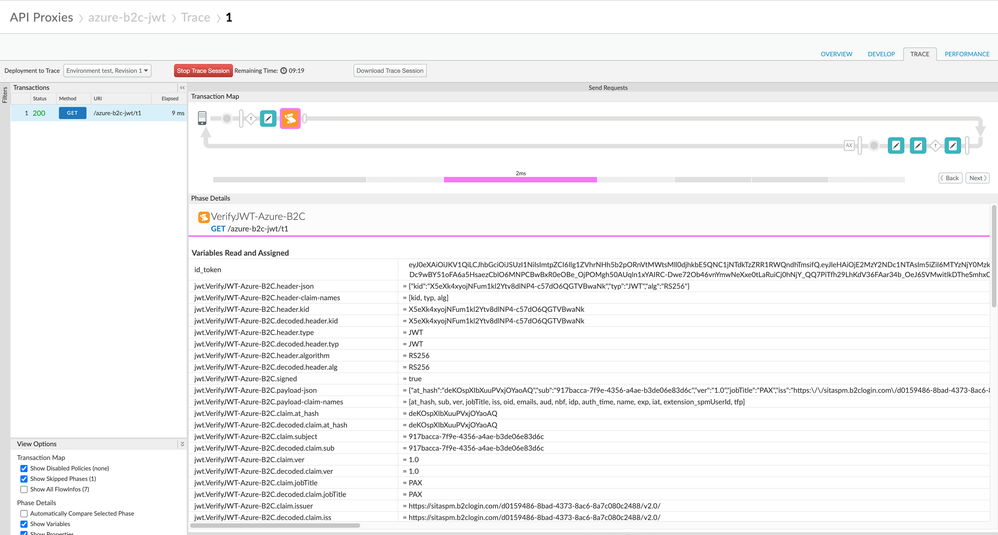
Attached please find the API proxy I used to test this out. Deploy it and invoke with curl -i $endpoint/azure-b2c-jwt/t1
I suspect you don't have your variables set just as you think. If the id_token has a Bearer prefix, then it won't work. If the id_token variable is not set, then VerifyJWT will throw a fault. In any case of VerifyJWT throwing a fault, You can find the error message in the trace. Look for the variable with suffix ".error" .
Good luck!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @dchiesa1
You are correct the value being verified was not clean string .
THe azure b2c token response actually returns multiple values in response :
"access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6Ilg1ZVhrNHh5b2pORnVtMWtsMll0djhkbE5QNC1jNTdkTzZRR1RWQndhTmsifQ.eyJpc3MiOiJodHRwczovL3NpdGFzcG0uYjJjbG9naW4uY29tL2QwMTU5NDg2LThiYWQtNDM3My04YWM2LThhN2MwODBjMjQ4OC92Mi4wLyIsImV4cCI6MTYzNjYzMzg4MCwibmJmIjoxNjM2NjMwMjgwLCJhdWQiOiIzMWU2MjQxZS00YjYxLTRmZjYtODZlYy05NzRjNjliMWE5NzQiLCJpZHAiOiJMb2NhbEFjY291bnQiLCJvaWQiOiI5MTdiYWNjYS03ZjllLTQzNTYtYTRhZS1iM2RlMDZlODNkNmMiLCJzdWIiOiI5MTdiYWNjYS03ZjllLTQzNTYtYTRhZS1iM2RlMDZlODNkNmMiLCJuYW1lIjoiQjItYmIyYWNjb3VudDc1N0B0ZXN0LmNvbSIsImpvYlRpdGxlIjoiUEFYIiwiZXh0ZW5zaW9uX3NwbVVzZXJJZCI6IjYxOGJmZGNhMDc1NTdkMDc4N2FjNmM4NSIsImVtYWlscyI6WyJCMi1iYjJhY2NvdW50NzU3QHRlc3QuY29tIl0sInRmcCI6IkIyQ18xX1JPUENfQXV0aCIsImF6cCI6IjMxZTYyNDFlLTRiNjEtNGZmNi04NmVjLTk3NGM2OWIxYTk3NCIsInZlciI6IjEuMCIsImlhdCI6MTYzNjYzMDI4MH0.XobXMHQkhQlDP_70bFbkobKO1qUDzjwzWKfBhq4kNzDRoSaV9KuPexSX5dr283KHUHGPdVSqlJRRoy2863qqXY-ANGB-mO9zjYvAa7cjshlsVNSpSWE1NEqzP2TVriFjTYNA0hO5CYjxtE1ibbNjskGxji85-ZEkIJTFPVOJVsnNFQ3LmqyB-aTPfqNVgJZ_hGzLD9No2Bq_6MS1uP4Wav3pMMxnCm20NQ100yWYXfawyrvQGso11qutVUreP41cD6yExntXSNNh05HyMY5uzf6mT_n7Kcp9y7ecU7xzzRMgYncJumnJ0k1sGi80xvOk7CsIURbB3PZT1yqqhUzFoQ",
"token_type": "Bearer",
"expires_in": "3600",
"refresh_token": "eyJraWQiOiJjcGltY29yZV8wOTI1MjAxNSIsInZlciI6IjEuMCIsInppcCI6IkRlZmxhdGUiLCJzZXIiOiIxLjAifQ..KpzPokHaMLq8IlVv.9lyyhMbOKaeQW9ChLBt3eQ5JZ1Y1U26T6-AU8Y7uf4oMw1iSb1aGjFkTfEVvXwTu7RKPa6bnsyoDiajXBLui2witHmMeNV9LzX-W8uwKva_eloDh5DjWKGpc1moJxsqGlo1IIo6Kyojx348KLOpc-vEAHBJe9Orz2koV0sbQnPI_R05VJUIFIxrsH2XitA0g9Gt6yY-5OZOtSb56lZgL4tVyM5Vem2Xlb1KHvNiST9ySKGhcoP9Q_XpsysSapdp9zT3HF6yBRo7yFbbWnNKeKKssEkSDd42phi28O2sE2D0X8p1B7YG-VMmlPeMp-AmvUgQOrSKvXQ4IV3QIaFBnSmRTnnaRZCDXZGNnyi3OohYp4Y7ebvAfeilPZZD5y8Y7eIoHpRVn1BHUMbT9o4PTpgajPa1UbIGpo6xpirAWdlPubJVOaXRoNCYgS0h_SMFixbc95T8j2axZTU9xEV2I6m9AKVaHn8z3Vd6gaKyZOopTuEgeG9E_-SZc8-PB64pIFHxPHZd7Wyx8umHAX6Dl_7xlT30HE-Z4TgAyT8lalVPX3Psd_da2P80h4Zl_fcTZoF_ikiOKO0_YVZiorEkVF70RWNwPC9x2ukZPTSHrNa6QuPv1M5BQ9tZSM6dbJ7ekP9f6Zx2-gxAYNJ3tIEkihnnto0WWr-eChHSbzZQPthG4k_qoQkYFKLYCNegJLyRJnbFfNGyKNCBnDOJqGeNIvSBw0IXbzOOXXhBsDvxAU2NM.8TNzHYd0bgPAfVF2wFf_iw",
"id_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6Ilg1ZVhrNHh5b2pORnVtMWtsMll0djhkbE5QNC1jNTdkTzZRR1RWQndhTmsifQ.eyJleHAiOjE2MzY2MzM4ODAsIm5iZiI6MTYzNjYzMDI4MCwidmVyIjoiMS4wIiwiaXNzIjoiaHR0cHM6Ly9zaXRhc3BtLmIyY2xvZ2luLmNvbS9kMDE1OTQ4Ni04YmFkLTQzNzMtOGFjNi04YTdjMDgwYzI0ODgvdjIuMC8iLCJzdWIiOiI5MTdiYWNjYS03ZjllLTQzNTYtYTRhZS1iM2RlMDZlODNkNmMiLCJhdWQiOiIzMWU2MjQxZS00YjYxLTRmZjYtODZlYy05NzRjNjliMWE5NzQiLCJpYXQiOjE2MzY2MzAyODAsImF1dGhfdGltZSI6MTYzNjYzMDI4MCwiaWRwIjoiTG9jYWxBY2NvdW50Iiwib2lkIjoiOTE3YmFjY2EtN2Y5ZS00MzU2LWE0YWUtYjNkZTA2ZTgzZDZjIiwibmFtZSI6IkIyLWJiMmFjY291bnQ3NTdAdGVzdC5jb20iLCJqb2JUaXRsZSI6IlBBWCIsImV4dGVuc2lvbl9zcG1Vc2VySWQiOiI2MThiZmRjYTA3NTU3ZDA3ODdhYzZjODUiLCJlbWFpbHMiOlsiQjItYmIyYWNjb3VudDc1N0B0ZXN0LmNvbSJdLCJ0ZnAiOiJCMkNfMV9ST1BDX0F1dGgiLCJhdF9oYXNoIjoiX1VocnNGUXJXMjh2dG5sSGF1VjdKdyJ9.JhouuYVQyJ6oLDlweJGy2YzSVDDLyW3o5XIT7-Xdm0HVUEUqKH19UvM5NUuvERMAO4iWHCMobzoV7eGVvlWJfekTu33355x_E7Ket4y4u3F5_j6_mRRFMsAmU19_-P-D9hfIbGvWgfDQ1P6zgGrfJ6_UqlSZK3aPVtmXIFNHzspEyLtIESFEjMZ8G_6AJYhdMHKBp6U-Ua1B9FTdh7H4OP6tJ_5qc5-kKWxsU1RQl4Tz2fK673e6UYvK51OG1IMUNcaxCxZdjbS7IG01mrs4NILki17NXjaeQTsot3NsQmK7X1VXLtorjGwVZjcbKseoj48GaVXWY2y9tBTJPO_xsA"
Using JS policy to extract required value set the token wrapped in quotes " " in the context variable id_token .
Removing the quotes in the assignment cleaned it up and now it is verifying as expected .
context.setVariable('id_token', JSON.stringify(azureResponse.access_token).replace('"',''));I can also verify using the published keys endpoint now which is elegant solution .
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<VerifyJWT async="false" continueOnError="false" enabled="true" name="Verify-JWT-Azure-B2C">
<DisplayName>Verify JWT-Azure-B2C</DisplayName>
<Algorithm>RS256</Algorithm>
<Source>id_token</Source>
<PublicKey>
<JWKS uri="https://sitaspm.b2clogin.com/sitaspm.onmicrosoft.com/b2c_1_signupsignin1/discovery/v2.0/keys"/>
</PublicKey>
<TimeAllowance>30s</TimeAllowance>
</VerifyJWT>
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Glad to hear you got it sorted.
BTW this line
context.setVariable('id_token', JSON.stringify(azureResponse.access_token).replace('"',''));
...could be replaced with
context.setVariable('id_token', azureResponse.access_token);
The JSON.stringify() is adding the quotes, and then you remove them afterwards.... you can skip both of those steps. It will work either way of course, but the second way feels cleaner to me.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,665 -
API Security
178 -
Apigee General
3,041 -
Apigee X
1,288 -
Developer Portal
1,910 -
Drupal Portal
43 -
Hybrid
463 -
Integrated Developer Portal
89 -
Integration
310 -
PAYG
13 -
Private Cloud Deployment
1,069 -
User Interface
77

 Twitter
Twitter