- Google Cloud
- :
- Cloud Forums
- :
- Apigee
- :
- Re: Integrating Apigee proxy URL to validate JWT f...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Team,
We are using Azure AD to authenticate user in our back end Application by JWT token, same functionality we want to implement using Apigee proxy URL to access our back end application using Azure AD JWT token but we are getting following error "Invalid serialized JWE object: Missing fourth delimiter"
Pease see below screenshot :
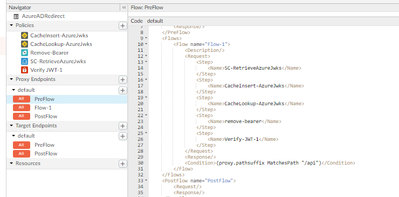
Below is our policy configuration
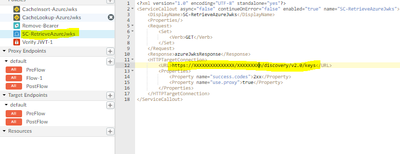
Step 1: First policy is to fetch the key details from public faced URL (Azure AD):
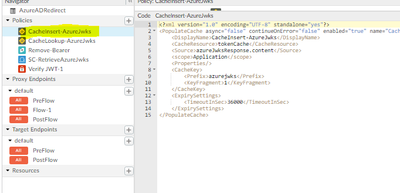
Step 2 : In second policy we are caching response from the step 1.
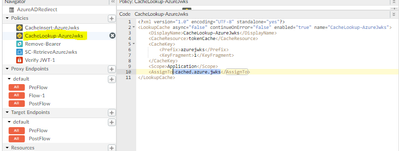
Step 3: In Third policy we are performing the cache lookup operation
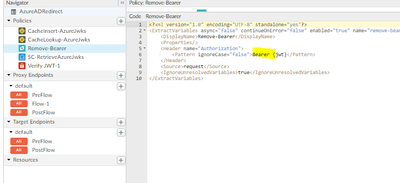
Step 4: In fourth policy we are removing the keyword "Bearer" from client request header and retaining the JWT token.
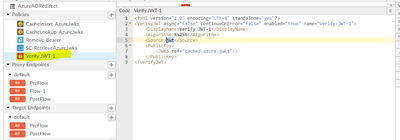
Step 5 : In fifth policy we are trying to verify the token with the cache public key from step 3.
Now we are using postman to hit proxy URL and using JWT token generated by our Azure AD.
This is our response :
- Labels:
-
User Interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you considered using the PublicKey/JWKS element of the VerifyJWT policy? It will retrieve and cache (300 secs) the JWKS from a public URI for you. Also, when validating a JWT, Apigee will by default, retrieve the JWT from the Authorization header - including stripping the Bearer prefix.
I'm thinking you could replace your current flow policies with a single VerifyJWT policy. For example, the below VerifyJWT policy will validate a JWT from Google Identity using its public JWKS:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<VerifyJWT name="JWT-Verify-RS256">
<Algorithm>RS256</Algorithm>
<IgnoreUnresolvedVariables>false</IgnoreUnresolvedVariables>
<PublicKey>
<JWKS uri="https://www.googleapis.com/oauth2/v3/certs"/>
</PublicKey>
<Subject>some-subject</Subject>
<Issuer>https://accounts.google.com</Issuer>
<Audience>some-audience</Audience>
</VerifyJWT>
-
Analytics
497 -
API Hub
75 -
API Runtime
11,665 -
API Security
178 -
Apigee General
3,041 -
Apigee X
1,288 -
Developer Portal
1,910 -
Drupal Portal
43 -
Hybrid
463 -
Integrated Developer Portal
89 -
Integration
310 -
PAYG
13 -
Private Cloud Deployment
1,069 -
User Interface
77

 Twitter
Twitter