- Google Cloud
- Cloud Forums
- Apigee
- How to link AccessToken to an User of Application.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AccessToken was issued on behalf of the user of the application. When the API request comes in with an user id, api-key and access-token, how do we validate if the access-token was issued to that user-id?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for clarifying @Pravin
You can use Custom Attributes as @Anil Sagar mentioned. The info is available here
While generating the Access token using the OAuth Policy, you can set the user info as custom attribute
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<OAuthV2 name="GenerateAccessTokenClient">
<Operation>GenerateAccessToken</Operation>
<!-- This is in millseconds, so expire in an hour -->
<ExpiresIn>3600000</ExpiresIn>
<SupportedGrantTypes>
<GrantType>authorization_code</GrantType>
<GrantType>client_credentials</GrantType>
<GrantType>implicit</GrantType>
<GrantType>password</GrantType>
</SupportedGrantTypes>
<GrantType>request.queryparam.grant_type</GrantType>
<ClientId>request.header.client_id</ClientId>
<RefreshTokenExpiresIn ref="refreshTokenExpiresIn">3600000</RefreshTokenExpiresIn>
<Attributes>
<Attribute name="userinfo.username" ref="userinfo.username"/> <!-- Provide the flow variable that has the value of the username for which the token is being generated -->
</Attributes>
<GenerateResponse/>
</OAuthV2>
Once you use the token generated and use this to call an API, the custom attribute will be available as a variable which can be used to validate the user info before accessing the data. My previous answer screenshot has a custom attribute - accesstoken.userinfo.username
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Pravin
After the VerifyAccessToken operation of OAuthV2 policy / Verify API Key policy is executed, a set of flow variables are available that can be used.
For VerifyAccessToken, the list of variables are listed here and for Verify API Key, the list of variables are listed here
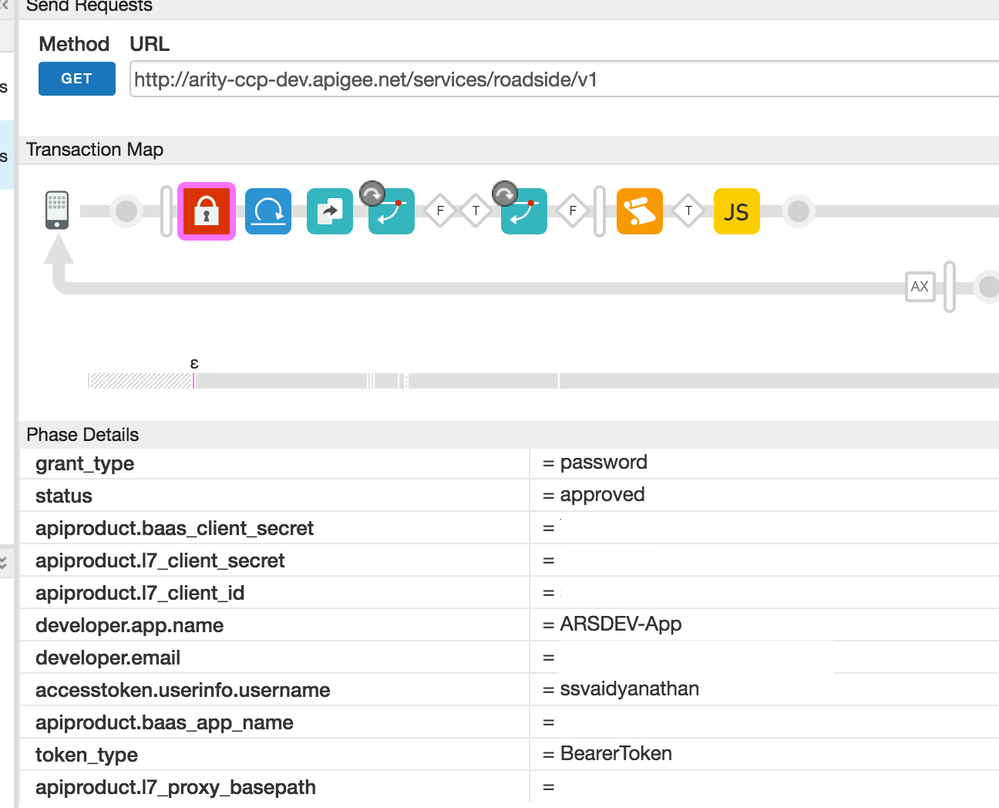
You can also find the values that are available using the Trace tool. After the API is executed, just click the policy (Verify API Key or OAuth) on the UI which will display the list of variables.
Please see screenshot below (have erased certain fields on the screenshot on purpose)
using these variables, you can check for the user id and raise a Fault using the Raise Fault policy
Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Pravin ,
Update : I believe you are talking about Application end user, We can leverage Access Token attributes & use them to validate in subsequent calls.
You can add a custom attribute called user id while generating access token & validate same in subsequent API calls to make sure he is the one who is calling same.
Find more info here. Keep us posted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Anil Sagar
Just added a comment to @Pravin question asking about the process in generating the token 🙂
As you mentioned, setting the custom attributes (for eg. user id - see my screenshot for attribute "accesstoken.userinfo.username) while Generating Access token and using it after VerifyAccessToken is the best approach
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI @Pravin
Also would be nice to know how the Access token is generated for a User (IDP, grant type, etc)?
In my answer below, I have assumed that Apigee is generating the OAuth token and using this token, a subsequent proxy in Apigee is called.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Anil Sagar And @Sai Saran Vaidyanathan for responses.
Lets me put the scenario I was looking for, in 3 leg OAuth user has authorized a 3rd party application to access Api (eventually data) on user's behalf. 3rd Party Application is a registered app, has client-id and client-secret. After completion of 3-leg Oauth flow 3rd party application got an access token which should be used only to access api to get that particular user's data. But Other users of same 3rd Party application can use same access token (if they able to get it -- somehow) to access apis...because on Edge VerifyAccessToken & Verify API Key policies are validating access token and not aware for which user that token was generated for. Basically VerifyAccessToken do not know about users of 3rd party application. so question was how to associate an access token to end users along with client_id and client_secret so that other user of same client-app not able to use it....
please do let me know if my problem statement is still not clear.... I will try again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for clarifying @Pravin
You can use Custom Attributes as @Anil Sagar mentioned. The info is available here
While generating the Access token using the OAuth Policy, you can set the user info as custom attribute
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<OAuthV2 name="GenerateAccessTokenClient">
<Operation>GenerateAccessToken</Operation>
<!-- This is in millseconds, so expire in an hour -->
<ExpiresIn>3600000</ExpiresIn>
<SupportedGrantTypes>
<GrantType>authorization_code</GrantType>
<GrantType>client_credentials</GrantType>
<GrantType>implicit</GrantType>
<GrantType>password</GrantType>
</SupportedGrantTypes>
<GrantType>request.queryparam.grant_type</GrantType>
<ClientId>request.header.client_id</ClientId>
<RefreshTokenExpiresIn ref="refreshTokenExpiresIn">3600000</RefreshTokenExpiresIn>
<Attributes>
<Attribute name="userinfo.username" ref="userinfo.username"/> <!-- Provide the flow variable that has the value of the username for which the token is being generated -->
</Attributes>
<GenerateResponse/>
</OAuthV2>
Once you use the token generated and use this to call an API, the custom attribute will be available as a variable which can be used to validate the user info before accessing the data. My previous answer screenshot has a custom attribute - accesstoken.userinfo.username
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Pravin - Did this answer your question ? If yes, please accept the answer.
If you still have questions, please reach out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you !
I will try this out and see if this approach answers all questions of our security team. I will update you on that.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,664 -
API Security
175 -
Apigee General
3,030 -
Apigee X
1,275 -
Developer Portal
1,907 -
Drupal Portal
43 -
Hybrid
461 -
Integrated Developer Portal
87 -
Integration
309 -
PAYG
13 -
Private Cloud Deployment
1,068 -
User Interface
75
| User | Count |
|---|---|
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter