- Google Cloud
- Cloud Forums
- Apigee
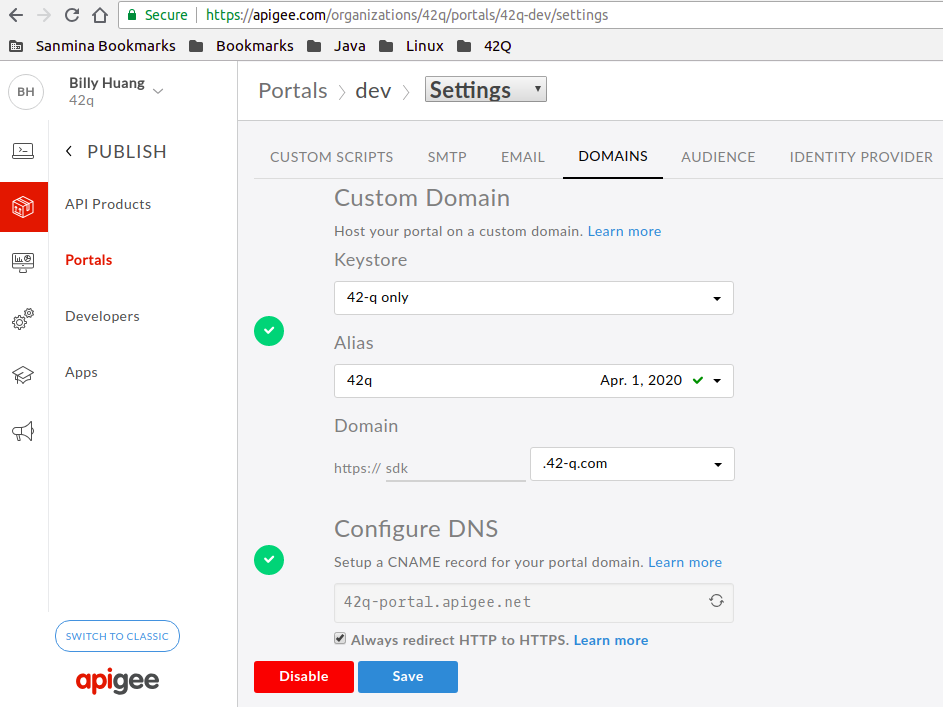
- Custom Domain 42q problem - URL: sdk.42-q.com
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
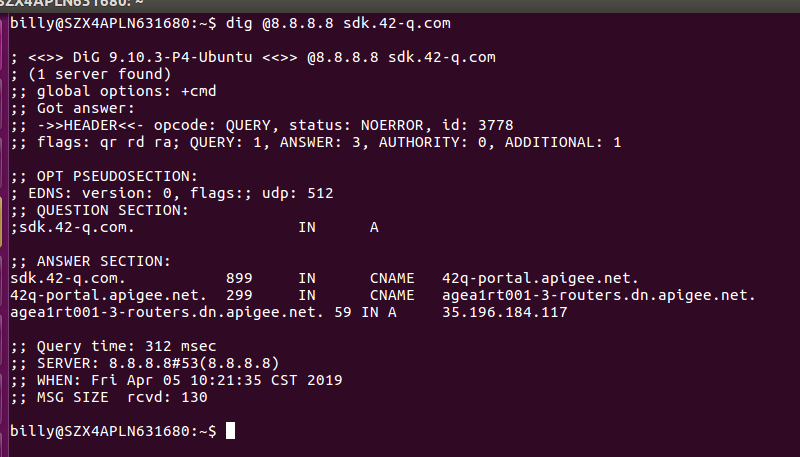
We have defined the custom domain follow up with https://docs-new.apigee.com/custom-domain but when we open the URL https://sdk.42-q.com on Chrome it always problem private issue.
Would you help to check where I am wrong which if I click the URL https://sdk.42-q.com on Chrome it always problem private issue.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This issue was fixed after contact Apigee support team and fix with below steps:
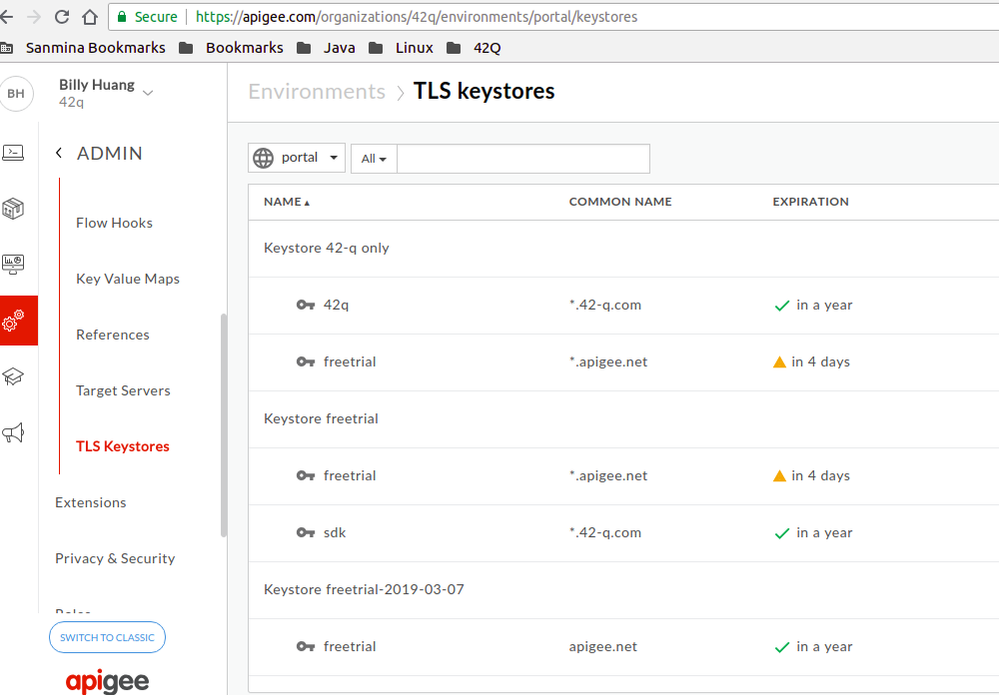
1. Removed SDK keystore from freetrial and freetrial-2019-03-07. P.S.: Apigee support team told me that should has same Certificate key for same keystore.
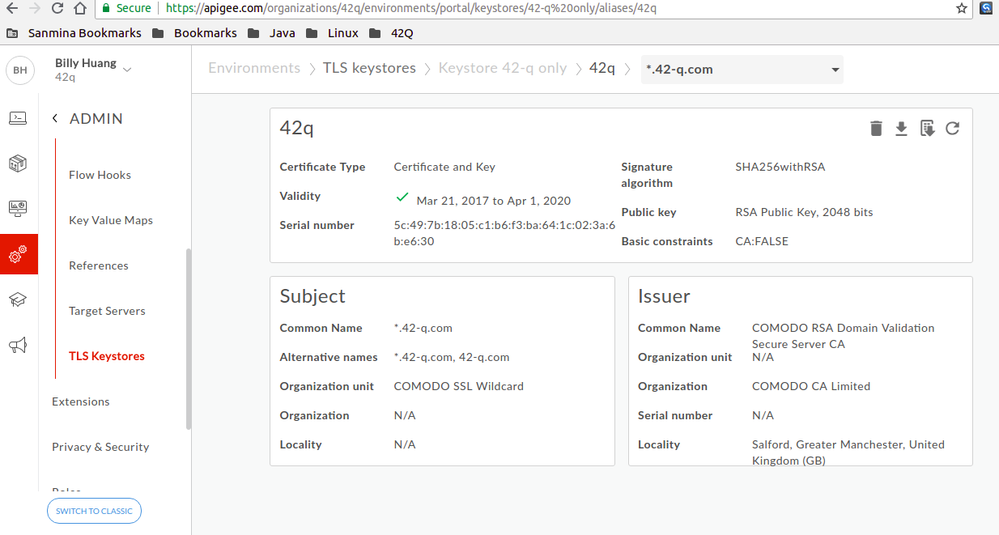
2. Create a new keystore and create a alias with type = "Certificate and Key" or type = "PKCS12/PFX File". In my case, I use PKCS12/PFX File.
3. Create a New Key Store Reference & Update The Virtual Host
4. Ask Apigee support team to restarted Apigee Routers of your Apigee organization and it reloaded the updated virtual host configuration.
Noted: This step is very important as Apigee support team told me that this issue may have occurred due to the invalid TLS keystore configuration which was given previously. So, please confirm right TLS keystore was configured on step 1~3 if you need create a new virutal host or portal with your domain names.
Appendix: The debug information from Apigee Support team
Above keystore reference is pointing to the below keystore:
...
{
"aliases" : [ {
"aliasName" : "apigateway-prod",
"cert" : "apigateway-prod-cert",
"key" : ""
}, {
"aliasName" : "freetrial",
"cert" : "freetrial-cert",
"key" : "freetrial-key"
} ],
"certs" : [ "freetrial-cert", "apigateway-dev-cert" ],
"keys" : [ "", "freetrial" ],
"name" : "freetrial-2019-03-07"
}
According to the above observation, it seems like you have used the freetrial keystore for providing the TLS certificate of the above virtual host (apigateway-dev.42-q.com).
As we found the same approach has taken in other environments; dev and test.
This is the reason why this problem has occurred.
Please try follow below steps to fix this issue in the dev environment first:
-------------------------
1. Create a New Key Store
-------------------------
- Log into New Edge UI and navigate to Admin -> Environments -> TLS Keystores:
https://apigee.com/organizations/42q/environments/dev/keystores
- Select dev environment
- Press +Keystore button to create a new Keystore using a new name (we could call this 42-q-keystore)
- Thereafter, press the plus button (Create alias button) on the above created keystore
- Specify a key alias name and select the Type as "Certificate and Key"
- Then select the complete TLS certificate chain including the public TLS certificate, intermediate certificates and root certificate. This should be in PEM format (if needed you could also use type as PKCS12/PFX and use a PKCS12/PFX file).
- Now, select the private key file of the above TLS certificate and specify the private key password and save.
-----------------------------------
2. Create a New Key Store Reference
-----------------------------------
- Navigate to New Edge UI -> Admin -> Environments -> References:
https://apigee.com/organizations/42q/environments/dev/references
- Select dev environment
- Press the +Reference button to create a new Keystore Reference
- Specify a new name (we could call this 42-q-keystore-ref) and select the above created keystore as the reference (42-q-keystore) and save
--------------------------
3. Update The Virtual Host
--------------------------
- Navigate to New Edge UI -> Admin -> Virtual Hosts:
https://apigee.com/organizations/42q/vhosts
- Select dev environment
- Select Virtual Host 42q which has host alias apigateway-dev.42-q.com
- Change the Keystore value to the above created Keystore Reference (ref://42-q-keystore-ref)
- Then, select the appropriate Keystore Alias and save.
- At this point, Apigee Routers of will get updated with the above TLS configuration.
-------------------------
4. Verify TLS Certificate
-------------------------
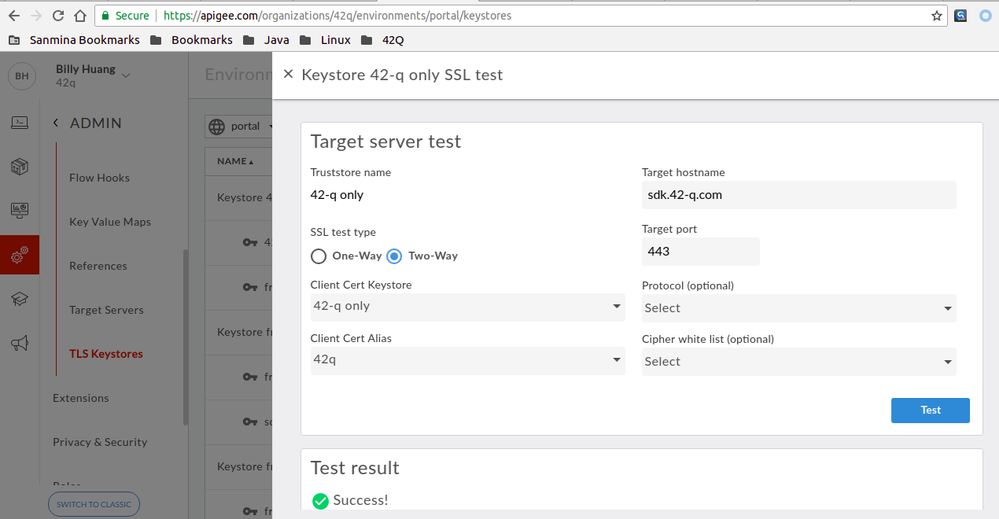
- Execute the below keytool [1] command on a Linux/OSX Shell to verify the TLS certificate of presented by domain "apigateway-dev.42-q.com". You would need JDK to be installed to have the keytool command to be available:
keytool -printcert -sslserver apigateway-dev.42-q.com:443
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Billy, you seems to have followed the correct steps but due to some reason the virtual host sdk.42-q.com:443 is returning *.apigee.net TLS certificate:
keytool -printcert -sslserver sdk.42-q.com:443 | sed -n -e 1,10p Certificate #0 ==================================== Owner: CN=*.apigee.net, OU=Domain Control Validated Issuer: CN=Go Daddy Secure Certificate Authority - G2, OU=http://certs.godaddy.com/repository/, O="GoDaddy.com, Inc.", L=Scottsdale, ST=Arizona, C=US Serial number: 4b379fe9a809fb0e Valid from: Thu Jan 14 04:25:54 AEDT 2016 until: Tue Apr 09 16:37:10 AEST 2019 Certificate fingerprints: SHA1: 9D:71:67:74:5D:D6:A9:88:C7:07:3A:B4:D4:9C:CB:9D:DD:8C:C8:84 SHA256: 0C:C2:D7:38:CD:FC:33:23:DB:C7:80:E2:15:69:71:A9:35:D4:9D:C1:E6:EC:9B:BF:9B:80:71:A1:B5:90:1F:47 Signature algorithm name: SHA256withRSA
I would recommend you to contact Apigee Support for this. The virtual host created by the dev portal may have not configured correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This issue was fixed after contact Apigee support team and fix with below steps:
1. Removed SDK keystore from freetrial and freetrial-2019-03-07. P.S.: Apigee support team told me that should has same Certificate key for same keystore.
2. Create a new keystore and create a alias with type = "Certificate and Key" or type = "PKCS12/PFX File". In my case, I use PKCS12/PFX File.
3. Create a New Key Store Reference & Update The Virtual Host
4. Ask Apigee support team to restarted Apigee Routers of your Apigee organization and it reloaded the updated virtual host configuration.
Noted: This step is very important as Apigee support team told me that this issue may have occurred due to the invalid TLS keystore configuration which was given previously. So, please confirm right TLS keystore was configured on step 1~3 if you need create a new virutal host or portal with your domain names.
Appendix: The debug information from Apigee Support team
Above keystore reference is pointing to the below keystore:
...
{
"aliases" : [ {
"aliasName" : "apigateway-prod",
"cert" : "apigateway-prod-cert",
"key" : ""
}, {
"aliasName" : "freetrial",
"cert" : "freetrial-cert",
"key" : "freetrial-key"
} ],
"certs" : [ "freetrial-cert", "apigateway-dev-cert" ],
"keys" : [ "", "freetrial" ],
"name" : "freetrial-2019-03-07"
}
According to the above observation, it seems like you have used the freetrial keystore for providing the TLS certificate of the above virtual host (apigateway-dev.42-q.com).
As we found the same approach has taken in other environments; dev and test.
This is the reason why this problem has occurred.
Please try follow below steps to fix this issue in the dev environment first:
-------------------------
1. Create a New Key Store
-------------------------
- Log into New Edge UI and navigate to Admin -> Environments -> TLS Keystores:
https://apigee.com/organizations/42q/environments/dev/keystores
- Select dev environment
- Press +Keystore button to create a new Keystore using a new name (we could call this 42-q-keystore)
- Thereafter, press the plus button (Create alias button) on the above created keystore
- Specify a key alias name and select the Type as "Certificate and Key"
- Then select the complete TLS certificate chain including the public TLS certificate, intermediate certificates and root certificate. This should be in PEM format (if needed you could also use type as PKCS12/PFX and use a PKCS12/PFX file).
- Now, select the private key file of the above TLS certificate and specify the private key password and save.
-----------------------------------
2. Create a New Key Store Reference
-----------------------------------
- Navigate to New Edge UI -> Admin -> Environments -> References:
https://apigee.com/organizations/42q/environments/dev/references
- Select dev environment
- Press the +Reference button to create a new Keystore Reference
- Specify a new name (we could call this 42-q-keystore-ref) and select the above created keystore as the reference (42-q-keystore) and save
--------------------------
3. Update The Virtual Host
--------------------------
- Navigate to New Edge UI -> Admin -> Virtual Hosts:
https://apigee.com/organizations/42q/vhosts
- Select dev environment
- Select Virtual Host 42q which has host alias apigateway-dev.42-q.com
- Change the Keystore value to the above created Keystore Reference (ref://42-q-keystore-ref)
- Then, select the appropriate Keystore Alias and save.
- At this point, Apigee Routers of will get updated with the above TLS configuration.
-------------------------
4. Verify TLS Certificate
-------------------------
- Execute the below keytool [1] command on a Linux/OSX Shell to verify the TLS certificate of presented by domain "apigateway-dev.42-q.com". You would need JDK to be installed to have the keytool command to be available:
keytool -printcert -sslserver apigateway-dev.42-q.com:443
-
Analytics
497 -
API Hub
75 -
API Runtime
11,664 -
API Security
175 -
Apigee General
3,030 -
Apigee X
1,275 -
Developer Portal
1,907 -
Drupal Portal
43 -
Hybrid
461 -
Integrated Developer Portal
87 -
Integration
309 -
PAYG
13 -
Private Cloud Deployment
1,068 -
User Interface
75
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter