- Google Cloud
- Cloud Forums
- Apigee
- ApigeeX - Proxy calling apigee apis as target with...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello folks,
I try to build a proxy that has to call https://apigee.googleapis.com/v1/ with the <Authentication> tag and a GCP service account that has the role Apigee Organization Admin.
https://hostname/proxy-name/v1/environments/XXX/keyvaluemaps
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<TargetEndpoint name="apigee-api">
<Description/>
<FaultRules/>
<PreFlow name="PreFlow">
<Request/>
<Response/>
</PreFlow>
<PostFlow name="PostFlow">
<Request/>
<Response/>
</PostFlow>
<Flows/>
<HTTPTargetConnection>
<Authentication>
<GoogleAccessToken>
<Scopes>
<Scope>https://www.googleapis.com/auth/cloud-platform</Scope>
</Scopes>
</GoogleAccessToken>
</Authentication>
<URL>https://apigee.googleapis.com/v1/organizations/******</URL>
</HTTPTargetConnection>
</TargetEndpoint>
When I deploy the proxy with the service account and test it, I receive this error :
{
"error": {
"code": 403,
"message": "Permission denied on resource \"organizations/gcp-apigee-hord-prod/environments/pub-dev1\" (or it may not exist)",
"status": "PERMISSION_DENIED"
}
}
- Labels:
-
Apigee X
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you calling across projects? (Across organizations) AFAIK That won't work. It's not stated as clearly as I would like in the documentation, but the documentation does say "Same project":
To make calls from a proxy, into a resource that is hosted in a different Google cloud project, you would need to do it "the old way" which is to explicitly obtain a token. You can do this by using ServiceCallout to invoke the https://oauth2.googleapis.com/token endpoint with a JWT (generated via GenerateJWT) signed with the Service Account private key, and passing in the grant_type of urn:ietf:params:oauth:grant-type:jwt-bearer. The response will be a token you can use to invoke any googleapis api, for which the service has access.
That might sound like a bunch of work. But take heart! Here is a re-usable SharedFlow that does this for you. All you need to do is deploy that sharedflow, provision your SA key into the KVM, insert a FlowCallout into your proxy, then embed the gcp-access-token variable into the Authentication header for your external call.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello !
I am calling from the same project I created the ApigeeX org.
So normally it should work. What's the problem then with my target ?
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't know. what I would check:
- check that the role of the user that deploys the proxy has actAs permissions
- check that the proxy really is deployed with that SA
- check that the SA actually has permissions on the Apigee organization. Eg, from the command line using gcloud, use the SA account to get an access token then invoke a REST call on the organization with that token.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- check that the role of the user that deploys the proxy has actAs permissions
=> How do you add this to your service account ? Can you pls show me with some screens ?
Thanks in advance !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
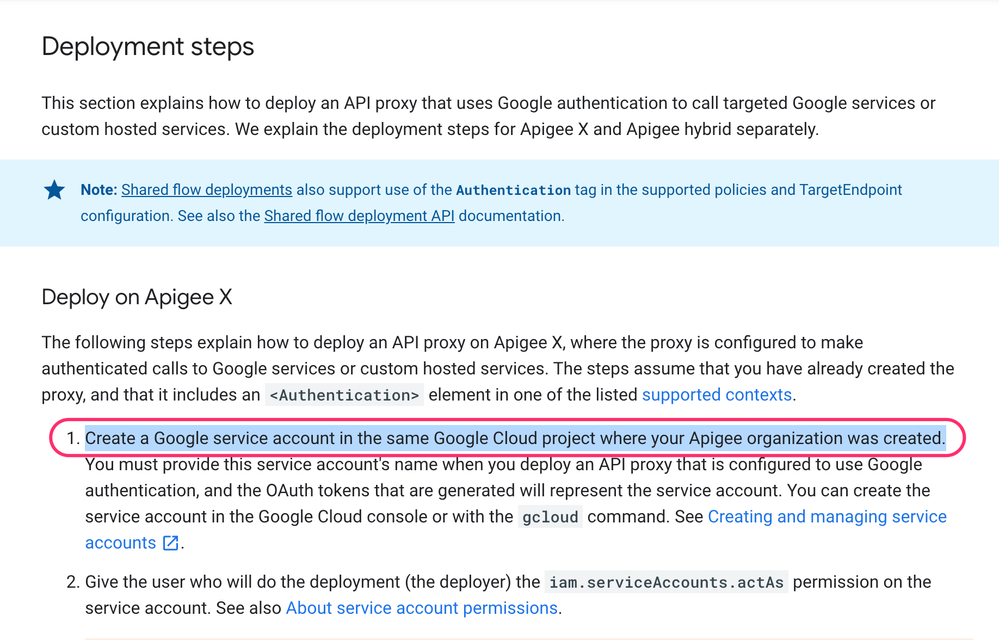
This page describes exactly what you need to do to set up the Service Account authentication.
-
Analytics
497 -
API Hub
75 -
API Runtime
11,664 -
API Security
177 -
Apigee General
3,036 -
Apigee X
1,283 -
Developer Portal
1,909 -
Drupal Portal
43 -
Hybrid
463 -
Integrated Developer Portal
89 -
Integration
309 -
PAYG
13 -
Private Cloud Deployment
1,068 -
User Interface
76
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |

 Twitter
Twitter