- Google Cloud
- Articles & Information
- Cloud Product Articles
- Auth0 with Apigee - External Authorization
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Use Case:
I have an external authorization server such as Auth0 or Oracle IDCS, which generates JWTs and the authorization code. I want my third-party authorization server to generate the authorization code and I want Apigee Edge to store and validate that code. Upon successful validation, the request should be sent to the third-party authorization server so that it can generate the JWT and return it back to the client through Edge. How do I implement this?
I would like to highlight that there is a great community article that describes how to integrate Edge with Auth0 here. My article covers how to implement this with External Authorization enabled for the OAuth 2.0 Authorization code flow. The implementation details are listed below.
Implementation Details
- auth0 external authorization proxy - contains all the proxy code and instructions to deploy the proxy, shared flows, developer, product and app into Apigee Edge.
- auth0 proxy contains three flows
- /authorize - validate the client ID and redirect, then forward the request to Auth0 to generate the authorization code
- /redirect - called by Auth0 and Edge stores the authorization code here
- /token - client uses this endpoint to exchange an authorization code for the JWT. Edge validates the authorization code, client ID, redirect URI and forwards the request to Auth0 to generate the JWT.
- JWT is NOT stored as an access token in Edge. (This should be a separate community article to show how to store the JWT in Edge.)
- Therefore, you must validate the JWT as specified in the community article pasted above.
- When you create an app in Auth0 the client ID and secret is generated for you. Those credentials should be created in Apigee Edge as well.
Auth0
The above community article describes how to configure Auth0 initially, so I will not describe all of those steps here. However, there some items that I would like to callout.
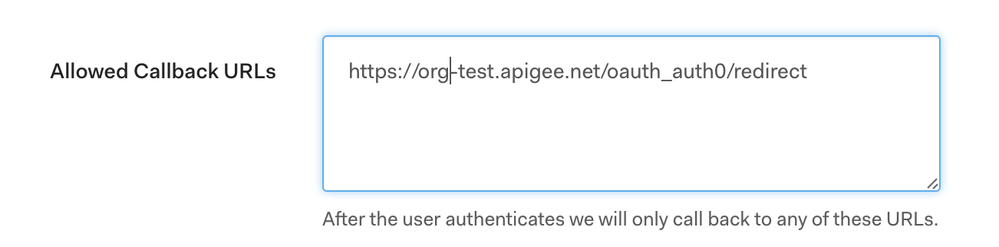
1) In the Allowed Callback URL, make sure to include the redirect URI to your auth0-oauth proxy. This will ensure that Auth0 will return the authorization code back to Edge so it can be stored there.
2) Create a user in Auth0, which is the user that you will use to login to Auth0 during the redirect step.
Deploy
Deploy the shared flows and the auth0-oauth proxy to Edge. When you deploy the auth0-oauth proxy it will automatically create the developer, product and developer app.
Add the Auth0 Client ID/Secret in Edge
After you deployed the auth0-oauth proxy, then you can add the client ID and secret from Auth0 into Edge.
1) Create the client ID and secret with the management API; the developer should be john@example.com. Use the client ID and secret from Auth0.
2) Associate the client ID and secret to an Edge product with the management API; the payload is below.
{ "apiProducts": ["auth0-product"] }Enable External Authorization Code
This section provides a high-level summary of the policies included in the auth0-oauth proxy.
/Authorization resource contains the following policy. Notice that the GenerateResponse enabled is set to false.
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<OAuthV2 async="false" continueOnError="false" enabled="true" name="OA-ValidateClientIdRedirect">
<DisplayName>OA-ValidateClientIdRedirect</DisplayName>
<Properties/>
<ResponseType>request.queryparam.response_type</ResponseType>
<ClientId>request.queryparam.client_id</ClientId>
<RedirectUri>request.queryparam.redirect_uri</RedirectUri>
<Scope>request.queryparam.scope</Scope>
<GenerateResponse enabled="false"/>
<Tokens/>
</OAuthV2>/redirect resource has a policy to extract the authorization code into a flow variable. Then it saves that authorization code in Edge.
StoreToken is set to true
ExternalAuthorization is set to true
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<OAuthV2 async="false" continueOnError="false" enabled="true" name="OA-StoreExternalAuthorizationCode">
<DisplayName>OA-StoreExternalAuthorizationCode</DisplayName>
<Operation>GenerateAuthorizationCode</Operation>
<ClientId>request.formparam.client_id</ClientId>
<ResponseType>response_type</ResponseType>
<GenerateResponse enabled="false"/>
<ExternalAuthorization>true</ExternalAuthorization>
<ExternalAuthorizationCode>request.formparam.code</ExternalAuthorizationCode>
<StoreToken>true</StoreToken>
<Tokens/>
</OAuthV2>/token resource has GenerateResponse set to false. It validates the client Id, redirect uri, etc. and then forwards the request to Auth0 to generate the JWT.
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<OAuthV2 async="false" continueOnError="false" enabled="true" name="OA-ValidateAccessCode">
<DisplayName>OA-ValidateAccessCode</DisplayName>
<Properties/>
<Attributes/>
<ExternalAuthorization>false</ExternalAuthorization>
<Operation>GenerateAccessToken</Operation>
<SupportedGrantTypes>
<GrantType>authorization_code</GrantType>
</SupportedGrantTypes>
<GenerateResponse enabled="false"/>
<Tokens/>
</OAuthV2>Demo and Trace
Start Apigee trace.
Modify the ORG and CLIENTID below to your Apigee Edge org and client ID, then paste this link into your browser.
https://ORG-test.apigee.net/oauth_auth0/authorize?client_id=CLIENTID&response_type=code&redirect_uri...
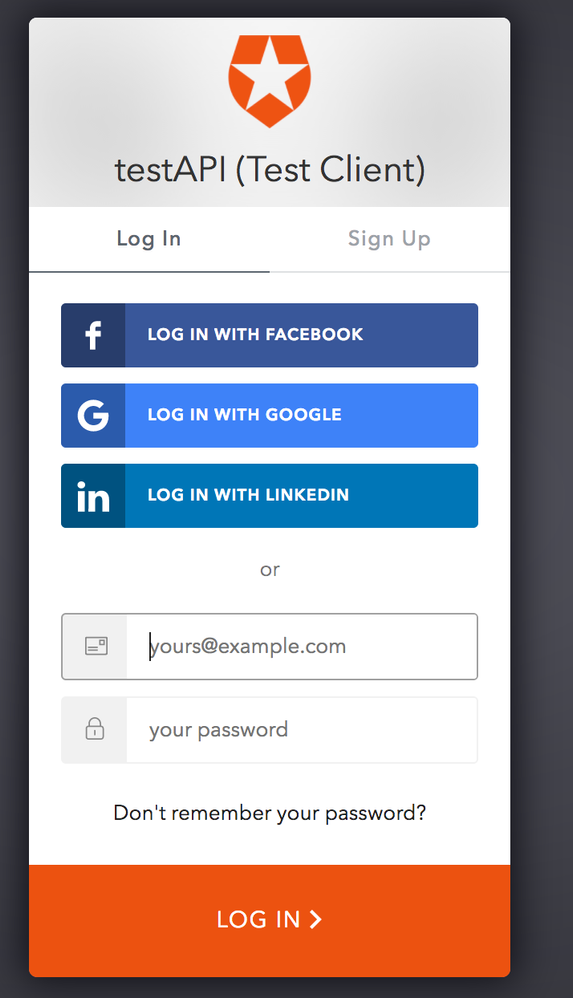
Your browser should be redirected to the Auth0 login page. Enter the username and password that you created in Auth0 and click login.
You should see the authorization code downloaded in your browser window. Copy the authorization code from this file or from the Apigee trace UI.
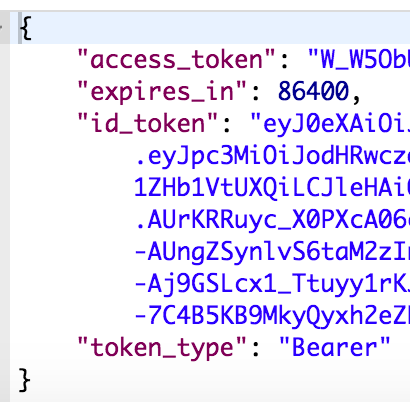
Paste the authorization code into the curl command below to obtain the JWT. Update the ORG, CLIENTID, AUTHCODE, CLIENTSECRET.
curl -X POST \ https://ORG-test.apigee.net/oauth_auth0/token \ -H 'content-type: application/x-www-form-urlencoded' \ -d 'client_id=CLIENTID&code=AUTHCODE&grant_type=authorization_code&redirect_uri=https%3A%2F%2Fcallback.io&client_secret=CLIENTSECRET'
Response should look something like...
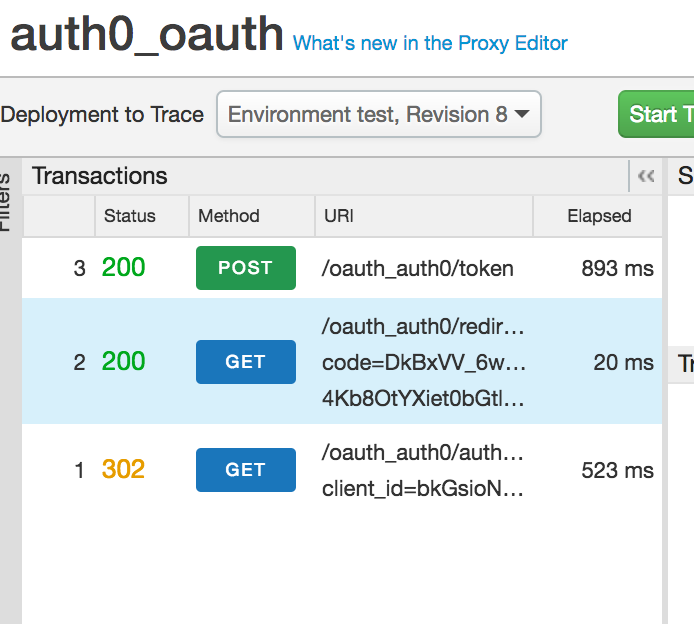
Apigee Trace - Authorization Code Flow
The following images shows the three requests within Edge.
1) This is the /authorize request which validates the client id and redirect URI and then forwards the request to Auth0. Auth0 sends a 302 redirect to the user's browser.
2) This is the /redirect request which is called by Auth0 after a successful login. This request flow also saves the authorization code in Edge.
3) This is the /token request to exchange the auth code for JWT. Edge validates the authorization code.
Now that you have the JWT, you can use this link to see how to validate the JWT within Apigee Edge or you can go directly to the JWT Java Callout Github repo and deploy the proxy to your Apigee org to validate the JWT.

 Twitter
Twitter