- Google Cloud
- Articles & Information
- Cloud Product Articles
- Dynamic SSLInfo for TargetEndpoint using variable ...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Apigee Edge API Management platform introduced a feature in the last cloud release 160120, whereby you could have variable references for keystore, keyalias etc. Please use this feature if you want to have these names dynamically set. The documentation is available here:
Here's an example. You can create a target endpoint definition like this:
<?xml version="1.0" encoding="UTF-8"?>
<HTTPTargetConnection>
<URL>https://api.mytarget.com</URL>
<SSLInfo>
<Enabled>{myvars.ssl.enabled}</Enabled>
<ClientAuthEnabled>{myvars.ssl.client.auth.enabled}</ClientAuthEnabled>
<KeyStore>{myvars.ssl.keystore}</KeyStore>
<KeyAlias>{myvars.ssl.keyAlias}</KeyAlias>
<TrustStore>{myvars.ssl.trustStore}</TrustStore>
</SSLInfo>
</HTTPTargetConnection>
Now you can have these variables defined in an assignMessage policy like this:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<AssignMessage async="false" continueOnError="false" enabled="true" name="SetSSLInfoVariables">
<DisplayName>SetSSLInfoVariables</DisplayName>
<Properties/>
<AssignVariable>
<Name>myvars.ssl.enabled</Name>
<Value>true</Value>
</AssignVariable>
<AssignVariable>
<Name>myvars.ssl.client.auth.enabled</Name>
<Value>true</Value>
</AssignVariable>
<AssignVariable>
<Name>myvars.ssl.keystore</Name>
<Value>freetrial</Value>
</AssignVariable>
<AssignVariable>
<Name>myvars.ssl.keyAlias</Name>
<Value>freetrial</Value>
</AssignVariable>
<AssignVariable>
<Name>myvars.ssl.trustStore</Name>
<Value>freetrial</Value>
</AssignVariable>
<IgnoreUnresolvedVariables>true</IgnoreUnresolvedVariables>
<AssignTo createNew="false" transport="http" type="request"/>
</AssignMessage>
How does this help ?
Imagine a scenario, where you are connecting to a backend endpoint over ssl and depending on whether you are connecting to the test or prod environment of that server you need to use appropriate keystore and truststores. With this feature it becomes really simple to do that, without having to change your proxy implementation all the time. Based on the request, have your API proxy evaluate which environment the API call needs to go to, then execute the appropriate Assign Message policy that sets the correct keystore and truststore values. The environment name is populated in the flow variable "environment.name".
I am also attaching the sample bundles that can help you explore this feature.
apigee-ssl: the proxy bundle that actually uses the dynamic keystore references apigee-ssl.zip
apigee-target: proxy bundle that acts as a mock backend which works over ssl apigee-target.zip
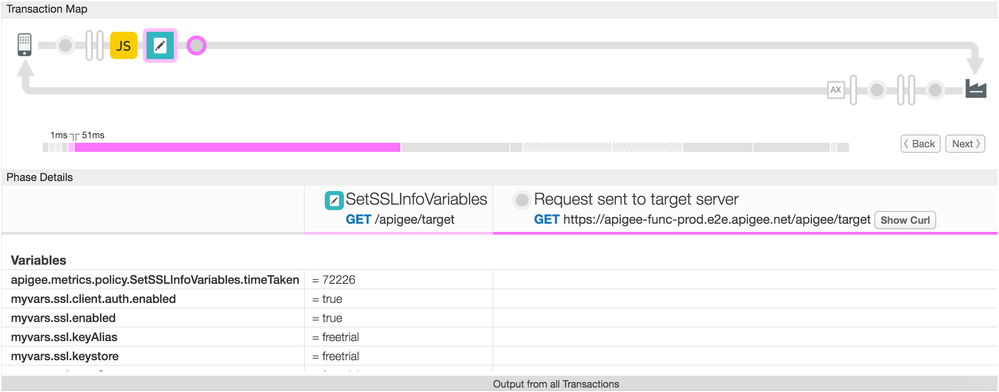
You can deploy these two bundles to your apigee orgs and try it for your self. It uses the default freetrial keystore that comes out of the box with your Edge org on the cloud. Here's a screenshot from trace showing how these variables get set and the call to the target is made:

 Twitter
Twitter