- Google Cloud
- Articles & Information
- Cloud Product Articles
- Apigee Drupal Dev Portal: Understanding Flood Cont...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
One of the security features that the Drupal Dev Portal comes with is flood control, which protects your site from brute force attacks. A brute force attack is an attempt to gain access to a site by inputting various user/password combinations until authorization is given.
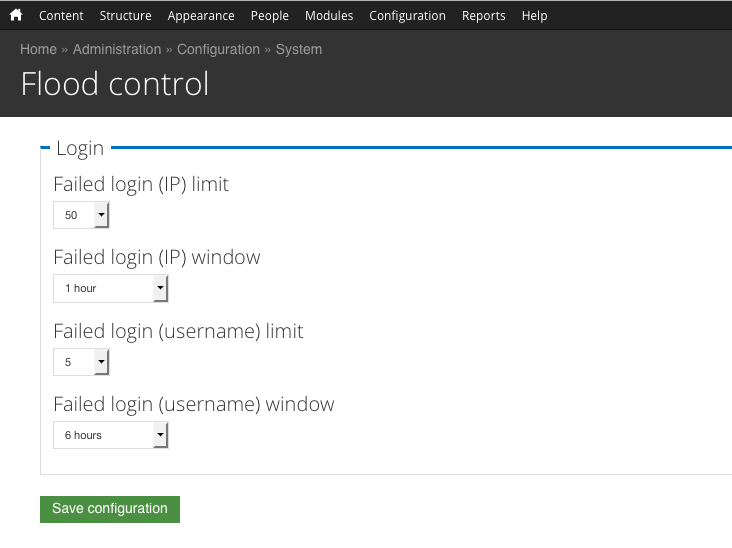
This feature is part of Drupal core, and Dev Portal installs with the Flood Control module enabled to give administrators a user interface to modify the default settings. To make changes, log in as a administrator and click on Configuration > System > Flood control.
As you can see in the screenshot above, if a user logs in incorrectly 5 times, they will be locked out for 6 hours. Note that changing these values to be less restrictive may be useful, but can also make your site more vulnerable to brute force attacks.
Viewing Flood Information
To view flood information, you need to go to the database or enable the Flood Report module.
If you enable Flood Report, you can go to Reports > Flood Reports to view the information in the table, or to flush the table.
If you want to use SQL, you can use the following commands:
mysql> select * from flood; +-----+---------------------------+------------------+------------+------------+| fid | event | identifier | timestamp | expiration |+-----+---------------------------+------------------+------------+------------+| 65 | failed_login_attempt_user | 49-51.204.252.36 | 1455043117 | 1455064717 || 67 | failed_login_attempt_user | 49-51.204.252.36 | 1455043230 | 1455064830 || 69 | failed_login_attempt_user | 49-51.204.252.36 | 1455043230 | 1455064830 || 72 | failed_login_attempt_user | 49-51.204.252.36 | 1455043239 | 1455064839 || 74 | failed_login_attempt_user | 49-51.204.252.36 | 1455043277 | 1455064877 |+-----+---------------------------+------------------+------------+------------+5 rows in set (0.10 sec)
You can see from the query above that user 49 with the IP 51.204.252.36 has records in the flood table. You can also look up the username for the user 49:
mysql> select name from users where uid=49; +----------+-----------------------------+ | name | mail | +----------+-----------------------------+ | juser | juser@example.com | +----------+-----------------------------+ 1 row in set (0.10 sec)
Unlocking Users
To unlock a user that is blocked, you either need to use a SQL command or enable the Flood Report module.
If you enable Flood Report, you can go to Reports > Flood Reports to view the information in the table, or to flush the table.
If you want to use SQL, the table 'flood' needs to be purged using the following SQL commands:
DELETE FROM `flood`; TRUNCATE flood RESTART IDENTITY;
The first command should work, but some users have reported that the second sql command is needed, and there isn't a problem running both.

 Twitter
Twitter